SonicWALL Internet Security Appliance Guide Page 123
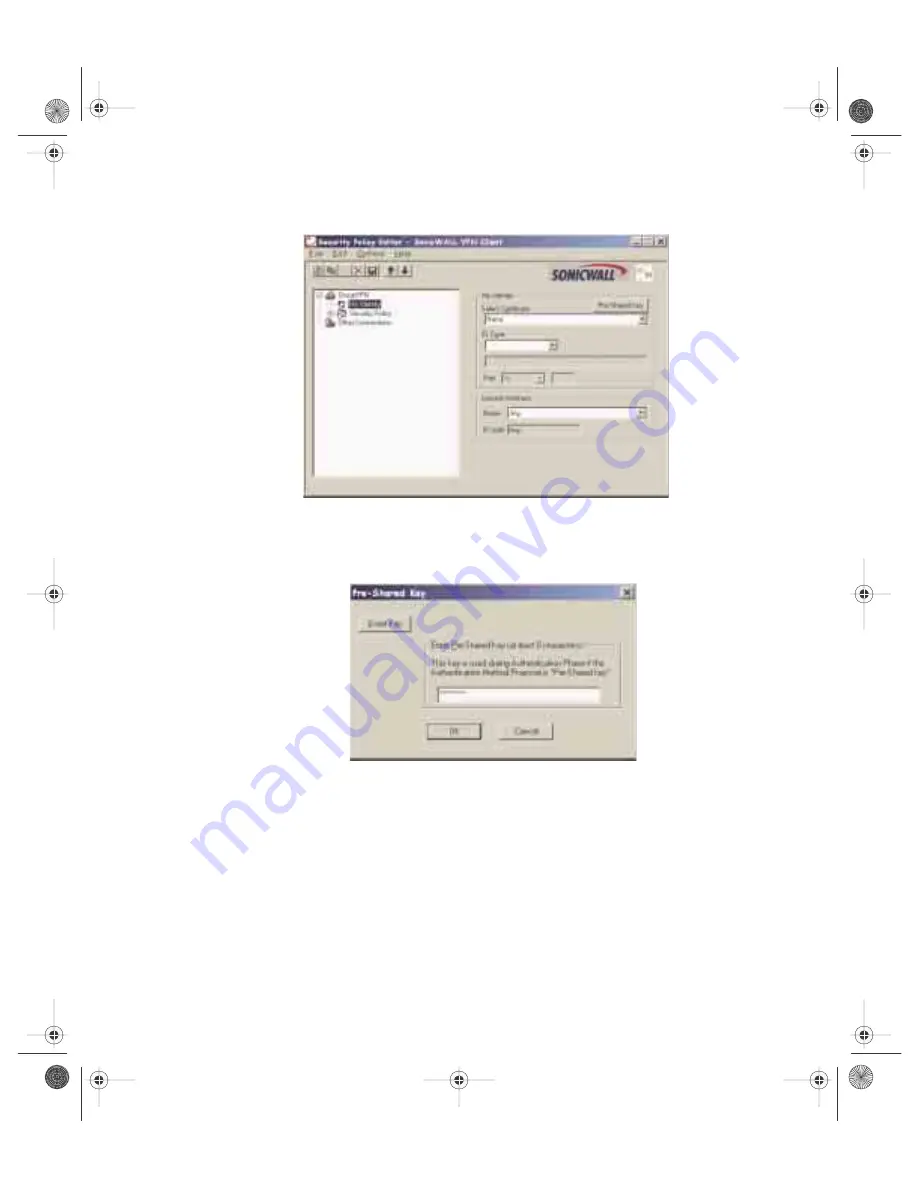
4. Click the
+
sign next to
Group VPN
to reveal two sections:
My Identity
and
Se-
curity Policy
. Select
My Identity
to view the settings.
5. Click
Pre-Shared Key
to enter the
Pre-Shared Secret
created in the
Group
VPN
settings in the SonicWALL appliance. Click
OK
.
6. Select
None
in the
Select Certificate
menu, and select
Domain Name
in the
ID Type
menu. Enter any word or phrase in the field below the
ID Type
menu.
Do not leave this field blank.
integrated_manual.book Page 123 Wednesday, June 13, 2001 6:21 PM






























