98 | SRA 6.0 Administrator’s Guide
Step 1
Navigate to the
System > Time
page.
Step 2
Select the
Automatically synchronize with an NTP server
check box.
Step 3
In the NTP Settings section, enter the time interval in seconds to synchronize time settings with
the NTP server in the
Update Interval
field. If no period is defined, the appliance will select the
default update interval, 3600 seconds.
Step 4
Enter the NTP server IP address or fully qualified domain name (FQDN) in the
NTP Server 1
field.
Step 5
For redundancy, enter a backup NTP server address in the
NTP Server Address 2 (Optional)
and
NTP Server Address 3 (Optional)
fields.
Step 6
Click
Accept
to update the configuration.
System > Settings
This section provides an overview of the
System > Settings
page and a description of the
configuration tasks available on this page.
•
“System > Settings Overview” section on page 98
•
“Managing Configuration Files” section on page 99
•
“Managing Firmware” section on page 101
System > Settings Overview
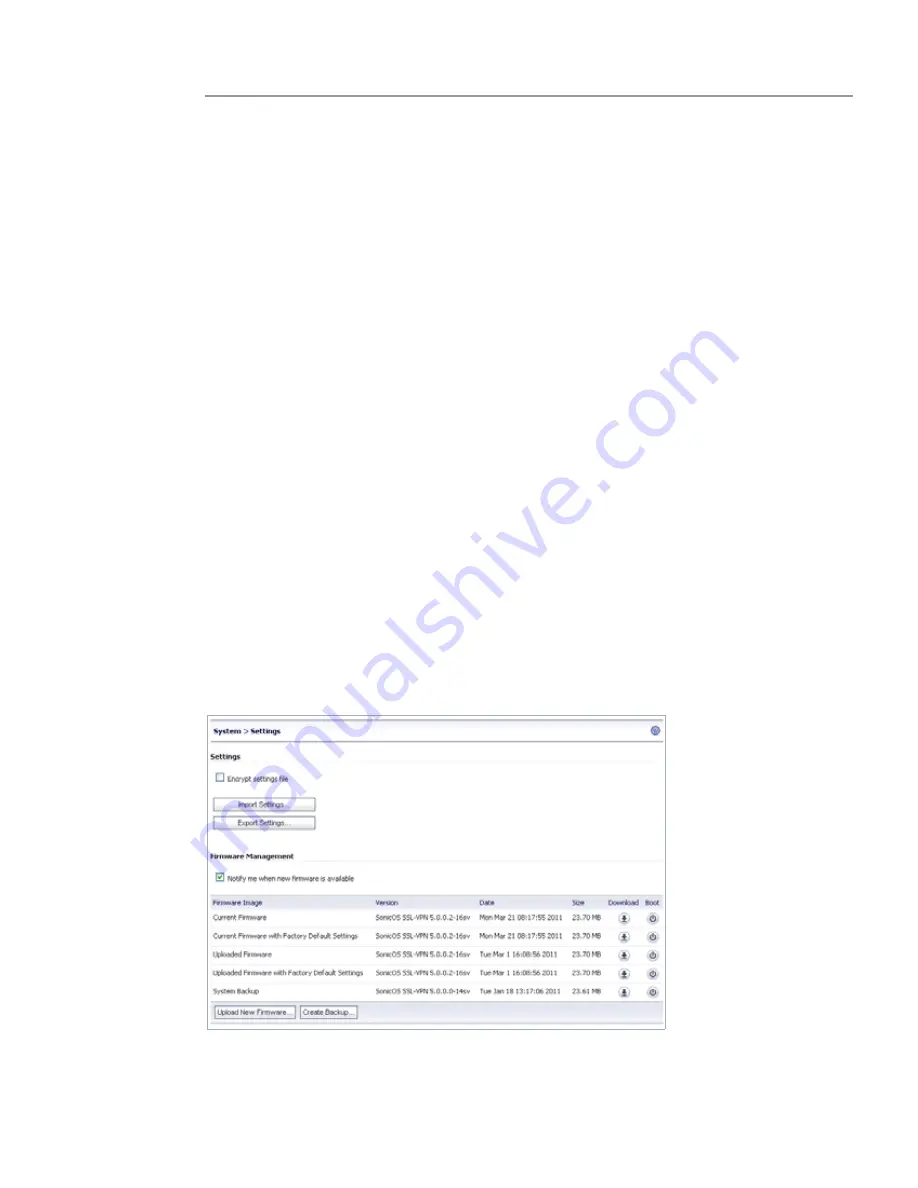
The
System
>
Settings
page allows the administrator to import and export the settings of the
SRA appliance.
On a physical appliance, the
System
>
Settings
page provides a way to upload new firmware,
and to boot either the current firmware, newly uploaded firmware, or backup firmware.
Figure 11
System > Settings Page - Physical Appliance
Summary of Contents for PowerEdge 4200 Series
Page 1: ... 1 SRA 6 0 Administrator s Guide ...
Page 10: ...10 SRA 6 0 Administrator s Guide ...
Page 128: ...128 SRA 6 0 Administrator s Guide ...
Page 176: ...176 SRA 6 0 Administrator s Guide ...
Page 190: ...190 SRA 6 0 Administrator s Guide ...
Page 212: ...212 SRA 6 0 Administrator s Guide ...
Page 228: ...228 SRA 6 0 Administrator s Guide ...
Page 342: ...342 SRA 6 0 Administrator s Guide ...
Page 356: ...356 SRA 6 0 Administrator s Guide ...
Page 358: ...358 SRA 6 0 Administrator s Guide ...
Page 392: ...392 SRA 6 0 Administrator s Guide ...
Page 416: ...416 SRA 6 0 Administrator s Guide ...
Page 426: ...426 SRA 6 0 Administrator s Guide ...
Page 436: ...436 SRA 6 0 Administrator s Guide ...
Page 438: ...438 SRA 6 0 Administrator s Guide ...
Page 439: ... 439 ...
Page 440: ......






























