Chapter 10 Interfaces
ZyWALL USG Series User’s Guide
375
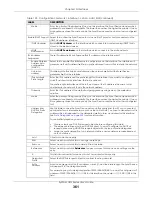
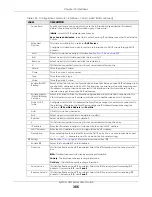
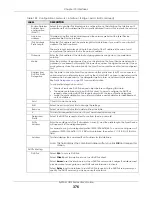
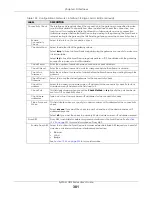
Description
Enter a description of this interface. You can use alphanumeric and
()+/:=?!*#@$_%-
characters, and it can be up to 60 characters long. Spaces are allowed, but the string
can’t start with a space.
Member
Configuration
Available
This field displays Ethernet interfaces and VLAN interfaces that can become part of the
bridge interface. An interface is not available in the following situations:
• There is a virtual interface on top of it
• It is already used in a different bridge interface
Select one, and click the
>>
arrow to add it to the bridge interface. Each bridge interface
can only have one VLAN interface.
Member
This field displays the interfaces that are part of the bridge interface. Select one, and click
the
<<
arrow to remove it from the bridge interface.
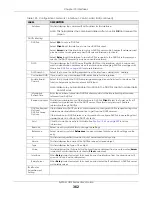
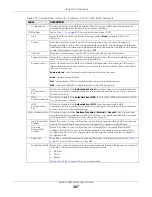
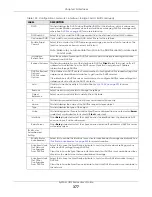
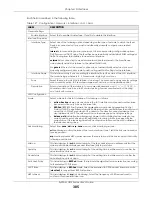
IP Address
Assignment
Get
Automatically
Select this if this interface is a DHCP client. In this case, the DHCP server configures the IP
address, subnet mask, and gateway automatically.
DHCP Option 60
DHCP Option 60 is used by the Zyxel Device for identification to the DHCP server using the
VCI (Vendor Class Identifier) on the DHCP server. The Zyxel Device adds it in the initial DHCP
discovery message that a DHCP client broadcasts in search of an IP address. The DHCP
server can assign different IP addresses or options to clients with the specific VCI or reject
the request from clients without the specific VCI.
Type a string using up to 64 of these characters [a-zA-Z0-9!\"#$%&\'()*+,-./
:;<=>?@\[\\\]^_`{|}~] to identify this Zyxel Device to the DHCP server. For example, Zyxel-
TW.
Use Fixed IP
Address
Select this if you want to specify the IP address, subnet mask, and gateway manually.
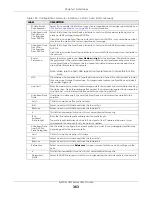
IP Address
This field is enabled if you select
Use Fixed IP Address
.
Enter the IP address for this interface.
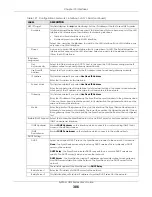
Subnet Mask
This field is enabled if you select
Use Fixed IP Address
.
Enter the subnet mask of this interface in dot decimal notation. The subnet mask indicates
what part of the IP address is the same for all computers in the network.
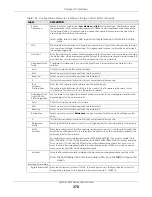
Gateway
This field is enabled if you select
Use Fixed IP Address
.
Enter the IP address of the gateway. The Zyxel Device sends packets to the gateway when
it does not know how to route the packet to its destination. The gateway should be on the
same network as the interface.
Metric
Enter the priority of the gateway (if any) on this interface. The Zyxel Device decides which
gateway to use based on this priority. The lower the number, the higher the priority. If two or
more gateways have the same priority, the Zyxel Device uses the one that was configured
first.
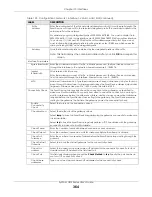
Enable IGMP Support Select this to allow the Zyxel Device to act as an IGMP proxy for hosts connected on the
IGMP downstream interface.
IGMP Upstream
Enable
IGMP Upstream
on the interface which connects to a router running IGMP that is
closer to the multicast server.
IGMP
Downstream
Enable
IGMP Downstream
on the interface which connects to the multicast hosts.
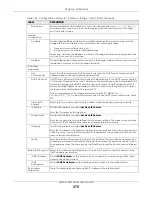
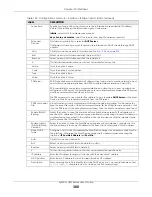
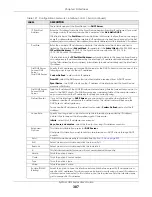
IPv6 Address
Assignment
These IP address fields configure an IPv6 IP address on the interface itself.
Table 125 Configuration > Network > Interface > Bridge > Add / Edit (continued)
LABEL
DESCRIPTION
Содержание USG110
Страница 27: ...27 PART I User s Guide ...
Страница 67: ...Chapter 2 Initial Setup Wizard ZyWALL USG Series User s Guide 67 Figure 41 Object Service Service Group HTTPS ...
Страница 195: ...195 PART II Technical Reference ...
Страница 282: ...Chapter 9 Wireless ZyWALL USG Series User s Guide 282 Figure 229 Configuration Wireless AP Management AP Group Add Edit ...
Страница 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Страница 310: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 310 Configuration Network Interface Ethernet Edit External Type ...
Страница 312: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 312 Configuration Network Interface Ethernet Edit Internal Type ...
Страница 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Страница 314: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 314 Figure 246 Configuration Network Interface Ethernet Edit OPT ...
Страница 315: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 315 Configuration Network Interface Ethernet Edit OPT ...
Страница 334: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 334 Figure 255 Configuration Network Interface PPP Add ...
Страница 342: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 342 Figure 257 Configuration Network Interface Cellular Add Edit ...
Страница 357: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 357 Figure 267 Configuration Network Interface VLAN Add Edit ...
Страница 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
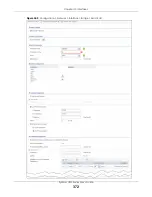
Страница 372: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 372 Figure 269 Configuration Network Interface Bridge Add Edit ...
Страница 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...
Страница 565: ...Chapter 25 Walled Garden ZyWALL USG Series User s Guide 565 Figure 399 Walled Garden Login Example ...
Страница 613: ...Chapter 30 IPSec VPN ZyWALL USG Series User s Guide 613 Figure 431 Configuration VPN IPSec VPN VPN Connection Add Edit ...
Страница 621: ...Chapter 30 IPSec VPN ZyWALL USG Series User s Guide 621 Figure 433 Configuration VPN IPSec VPN VPN Gateway Add Edit ...
Страница 651: ...Chapter 31 SSL VPN ZyWALL USG Series User s Guide 651 Figure 454 Create a Web Application SSL Application Object ...
Страница 664: ...Chapter 32 SSL User Screens ZyWALL USG Series User s Guide 664 4 Next run and log into the SecuExtender client ...
Страница 730: ...Chapter 38 IDP ZyWALL USG Series User s Guide 730 Figure 508 Configuration UTM Profile IDP Custom Signatures Add Edit ...
Страница 784: ...Chapter 42 Device HA ZyWALL USG Series User s Guide 784 Figure 541 Configuration Device HA Device HA ...
Страница 929: ...Chapter 44 System ZyWALL USG Series User s Guide 929 Figure 648 Configuration System WWW Login Page Desktop View ...
Страница 978: ...Chapter 45 Log and Report ZyWALL USG Series User s Guide 978 Figure 696 Log Category Settings AC ...
Страница 1011: ...Chapter 47 Diagnostics ZyWALL USG Series User s Guide 1011 Figure 720 Maintenance Diagnostics Network Tool ...