MANUAL TEST FUNCTIONS
61
-
When the network administrator, or one of the technicians, is suspect in setting up a
VoIP phone for unauthorized audio broadcast, then the Port Mirroring method can still
be utilized. However, instead of modifying any settings in the suspect router/switch, a
router/switch that has already been setup for Port Mirroring can be utilized.
o
Disconnect their router from the network
o
Patch it through your router
o
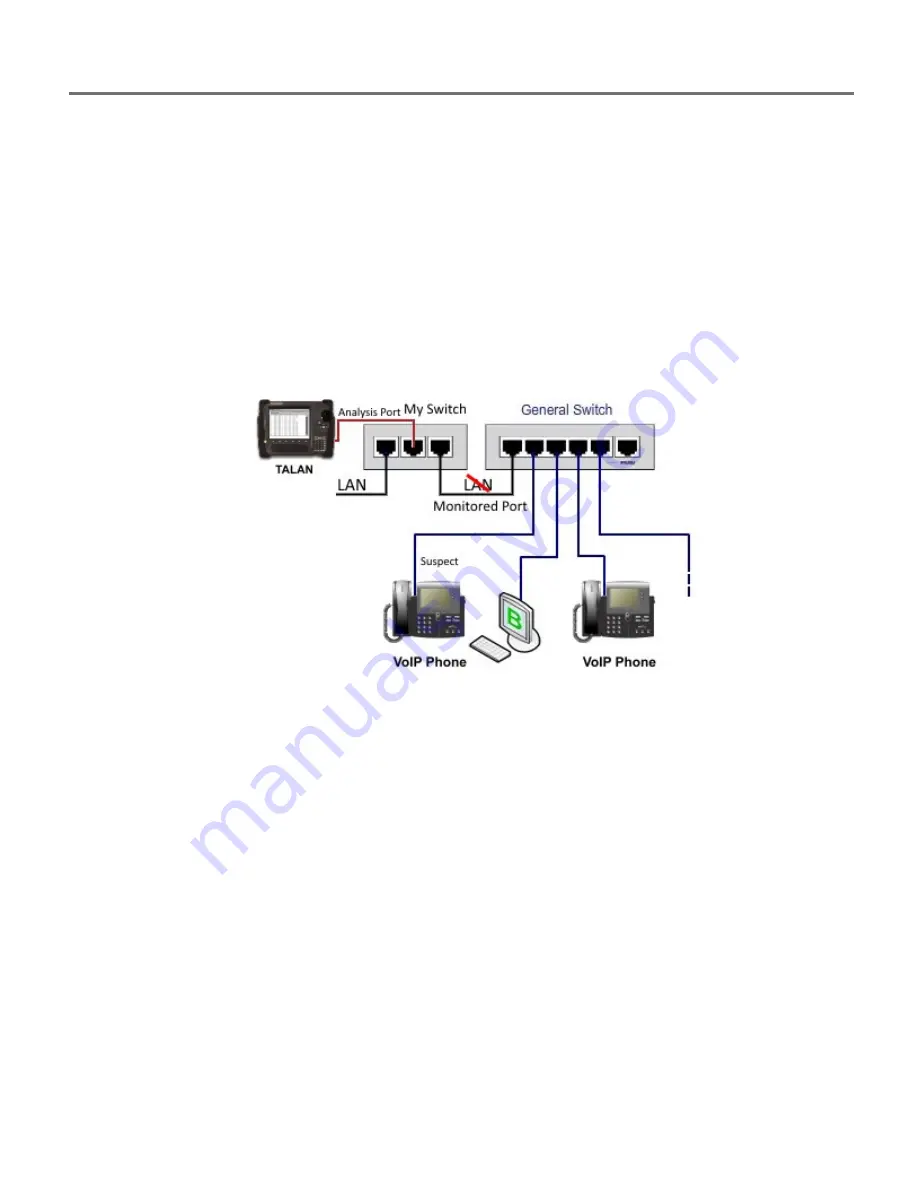
As shown below, the cable from the general switch that went to the LAN is now
connected to [My Switch], and [My Switch] is connected to the LAN. The middle
port shown would be set up with Port Mirroring, to monitor the port from the
General Switch:
The TALAN Ethernet Interface is set up so that it does not annunciate itself with the network
server, meaning, that the TALAN will not be detected by anything used to monitor network
access, including network monitoring packages such as wireshark or even the nework
administration / server software. However, the TALAN does work at the hardware layer so that
the when plugged into a switch or router, the hardware of that switch or router will make a
hardware level connection, but still is invisible to any other devices on the network. The
software and hardware in the TALAN are designed so that it will not transmit any packets of any
sort on the network. It is only a
listening
device so the network interface is non-alerting to
potential threats. This is a very big benefit when using the TALAN instead of a laptop to look for
illicit traffic. Laptops will be seen on the network by system administrators, whereas the TALAN
will not be visible on the network.
Содержание TALAN 3.0
Страница 2: ......
Страница 33: ...MANUAL TEST FUNCTIONS 33 Select the name of the data set you want to recall and select OK...






























