NAC quarantine and the Banned User list
User
FortiGate Version 4.0 Administration Guide
596
01-400-89802-20090424
When an interface is blocked by NAC quarantine or a DLP sensor with action set to
Quarantine Interface
, any user attempting to start an HTTP session through this interface
using TCP port 80 will also be connected by the FortiGate unit to one of the four NAC
quarantine web pages.
The DLP
Ban
and
Ban Sender
options also send messages to blocked users. For more
information, see
“Adding or editing a rule in a DLP sensor” on page 513
.
Configuring NAC quarantine
You can configure NAC quarantine for antivirus protection in a protection profile and for
IPS sensors and DoS sensors:
•
To configure NAC quarantine for antivirus protection, go to
Firewall > Protection
Profile
. Add or edit a protection profile and configure
Anti-Virus
. Enable
Quarantine
Virus Sender (to Banned Users List)
, select a
Method
, and configure
Expires
. For more
information, see
“Anti-Virus options” on page 407
.
•
To configure NAC quarantine for an IPS sensor, go to
UTM > Intrusion Protection >
IPS Sensor
. Add or edit an IPS sensor. To add NAC quarantine to a filter, select
Add
Filter
, enable
Quarantine Attackers (to Banned Users List)
select a
Method
, and
configure
Expires.
You can also add NAC quarantine to pre-defined and custom
overrides in an IPS sensor. For more information, see
“Configuring filters” on page 464
and
“Configuring pre-defined and custom overrides” on page 465
.
•
To configure NAC quarantine for a DoS sensor, you create or edit a DoS sensor and
from the CLI configure NAC quarantine for one or more of the 12 anomaly types. To
configure NAC quarantine for an anomaly, you set
quarantine
to
attacker
to block
the attacker,
both
to block both the attacker and the target, or
interface
to block the
interface that received the attack.
You can add the DoS sensor from the web-based manager or the CLI but you can only
configure NAC quarantine from the CLI. The following example shows how to edit a
DoS sensor named
QDoS_sensor
, set quarantine to
attacker
for the
udp_dst_session
and set the quarantine expiry time to 30 minutes. The example
also shows how to set quarantine to
both
for the
icmp_flood
anomaly:
config ips DoS
edit QDoS_sensor
config anomaly
edit udp_dst_session
set quarantine attacker
set quarantine-expiry 30
next
edit icmp_flood
set quarantine both
end
end
For more information, see the
.
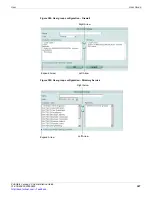
The Banned User list
The Banned User list shows all IP addresses and interfaces blocked by NAC quarantine.
The list also shows all IP addresses, authenticated users, senders, and interfaces blocked
by Data Leak Prevention (DLP). The system administrator can selectively release users or
interfaces from quarantine or configure quarantine to expire after a selected time period.
Содержание Gate 60D
Страница 678: ...Reports Log Report FortiGate Version 4 0 Administration Guide 678 01 400 89802 20090424 http docs fortinet com Feedback...
Страница 704: ...Index FortiGate Version 4 0 Administration Guide 704 01 400 89802 20090424 http docs fortinet com Feedback...
Страница 705: ...www fortinet com...
Страница 706: ...www fortinet com...