Adding NAT firewall policies in transparent mode
Firewall Virtual IP
FortiGate Version 4.0 Administration Guide
386
01-400-89802-20090424
Adding NAT firewall policies in transparent mode
Similar to operating in NAT/Route mode, when operating a FortiGate unit in Transparent
mode you can add firewall policies and:
•
Enable NAT to translate the source addresses of packets as they pass through the
FortiGate unit.
•
Add virtual IPs to translate destination addresses of packets as they pass through the
FortiGate unit.
•
Add IP pools as required for source address translation
For NAT firewall policies to work in NAT/Route mode you must have two interfaces on two
different networks with two different subnet addresses. Then you can create firewall
policies to translate source or destination addresses for packets as they are relayed by the
FortiGate unit from one interface to the other.
A FortiGate unit operating in Transparent mode normally has only one IP address, the
management IP. To support NAT in Transparent mode you can add a second
management IP. These two management IPs must be on different subnets. When you add
two management IP addresses, all FortiGate unit network interfaces will respond to
connections to both of these IP addresses.
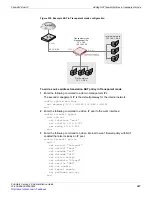
In the example shown in
, all of the PCs on the internal network (subnet
address 192.168.1.0/24) are configured with 192.168.1.99 as their default route. One of
the management IPs of the FortiGate unit is set to 192.168.1.99. This configuration results
in a typical NAT mode firewall. When a PC on the internal network attempts to connect to
the Internet, the PC's default route sends packets destined for the Internet to the FortiGate
unit internal interface.
Similarly on the DMZ network (subnet address 10.1.1.0/24) all of the PCs have a default
route of 10.1.1.99.
The example describes adding an internal to wan1 firewall policy to relay these packets
from the internal interface out the wan1 interface to the Internet. Because the wan1
interface does not have an IP address of its own, you must add an IP pool to the wan1
interface that translates the source addresses of the outgoing packets to an IP address on
the network connected to the wan1 interface.
The example describes adding an IP pool with a single IP address of 10.1.1.201. So all
packets sent by a PC on the internal network that are accepted by the internal to wan1
policy leave the wan1 interface with their source address translated to 10.1.1.201. These
packets can now travel across the Internet to their destination. Reply packets return to the
wan1 interface because they have a destination address of 10.1.1.201. The internal to
wan1 NAT policy translates the destination address of these return packets to the IP
address of the originating PC and sends them out the internal interface to the originating
PC.
Use the following steps to configure NAT in Transparent mode
•
Adding two management IPs
•
Adding an IP pool to the wan1 interface
•
Adding an internal to wan1 firewall policy
Содержание Gate 60D
Страница 678: ...Reports Log Report FortiGate Version 4 0 Administration Guide 678 01 400 89802 20090424 http docs fortinet com Feedback...
Страница 704: ...Index FortiGate Version 4 0 Administration Guide 704 01 400 89802 20090424 http docs fortinet com Feedback...
Страница 705: ...www fortinet com...
Страница 706: ...www fortinet com...