DES-3028 DES-3028P DES-3028G DES-3052 DES-3052P Layer 2 Fast Ethernet Managed Switch
Dynamic IP Multicast Learning
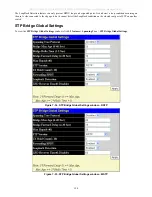
To configure the Dynamic IP Multicast Learning Max Entry Settings on the Switch, click
L2 Features
>
IGMP Snooping >
Dynamic IP Multicast Learning
.
Figure 7- 20. Dynamic IP Multicast Learning Settings window
107
Содержание DES-3028
Страница 306: ......
Страница 307: ......
Страница 327: ...D Link D Link D Link D Link 7 495 744 00 99 http www dlink ru e mail support dlink ru...
Страница 332: ...Technical Support Web Web URL http www dlink jp com...