DGS-3048 Gigabit Ethernet Switch Manual
Parameter
Description
Allowed to go port
Allows the selection of the port number on which the MAC address entered above
resides.
Click
Apply
to implement the changes made. To delete an entry in the Static Unicast Forwarding Table, click the
corresponding
under the Delete
heading.
Multicast Forwarding
The following window describes how to set up Multicast Forwarding on the Switch. Open the
Forwarding
folder and click
on the
Multicast Forwarding
link to see the entry window below:
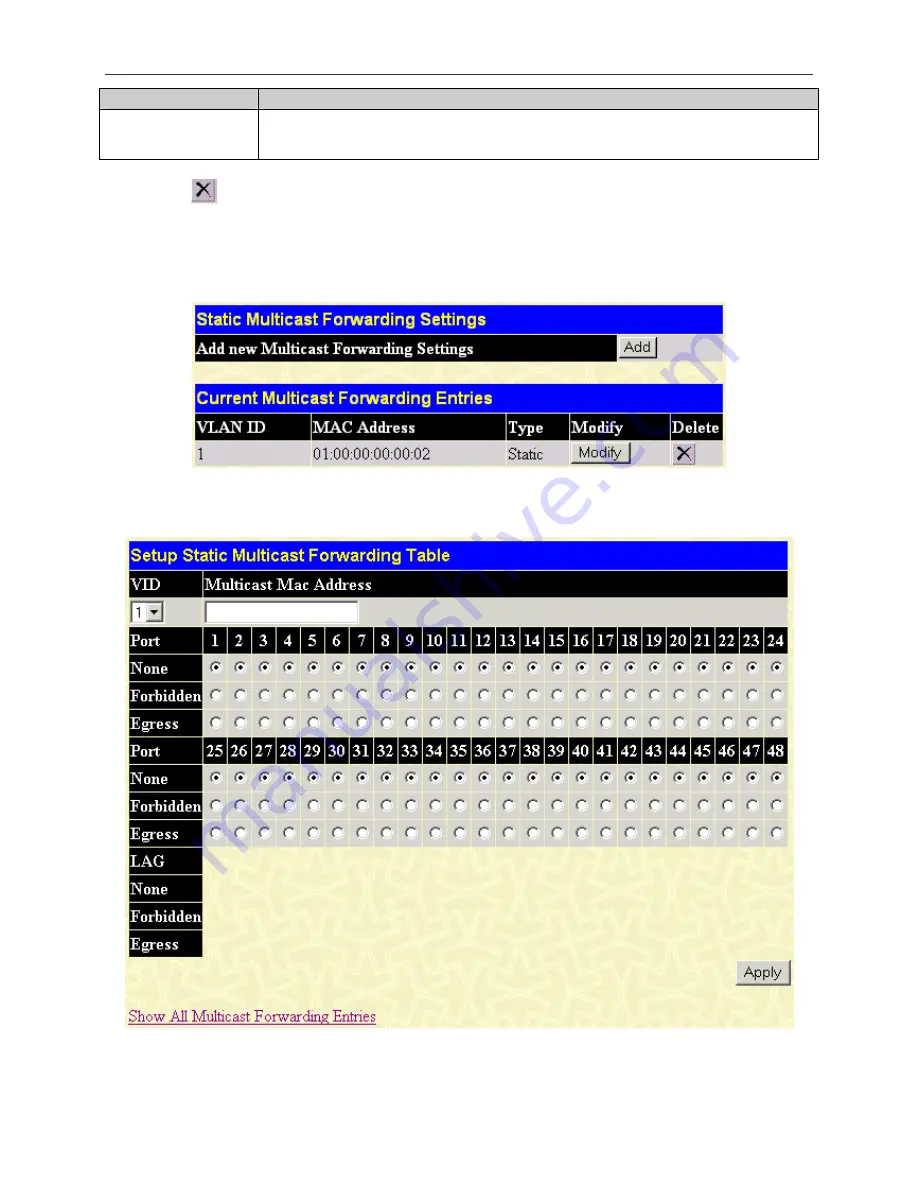
Figure 8- 17. Static Multicast Forwarding Settings Window
The
Static Multicast Forwarding Settings
window displays all of the entries made into the Switch's static multicast
forwarding table. Click the
Add
button to open the
Setup Static Multicast Forwarding Table
window, as shown below:
Figure 8- 18. Setup Static Multicast Forwarding Table Window
61
Содержание D DGS-3048 DGS-3048
Страница 1: ...D Link DGS 3048 Managed 48 Port Gigabit Ethernet Switch Manual ...
Страница 2: ......
Страница 29: ...DGS 3048 Gigabit Ethernet Switch Manual Figure 6 1 Enter Network Password Dialog Box 17 ...
Страница 146: ......
Страница 147: ......