DGS-3048 Gigabit Ethernet Switch Manual
20
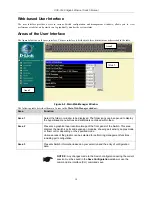
Switch 802.1x
The Switch’s 802.1x function may be enabled by port; the default is
Disabled
. This field
must be enabled to view and configure certain windows for 802.1x. More information
regarding 802.1x, its functions and implementation can be found later in this section,
under the Security
→
802.1x folder. Port-Based 802.1x specifies that ports configured
for 802.1x are initialized based on the port number only and are subject to any
authorization parameters configured.
Syslog State
This allows you to enable or disable the System Log State. The default is
enabled
.
Содержание D DGS-3048 DGS-3048
Страница 1: ...D Link DGS 3048 Managed 48 Port Gigabit Ethernet Switch Manual ...
Страница 2: ......
Страница 29: ...DGS 3048 Gigabit Ethernet Switch Manual Figure 6 1 Enter Network Password Dialog Box 17 ...
Страница 146: ......
Страница 147: ......