40
use the service, you must first apply an account from several free Web servers such as
www.dyndns.org, or www.TZO.com
DDNS Service
-
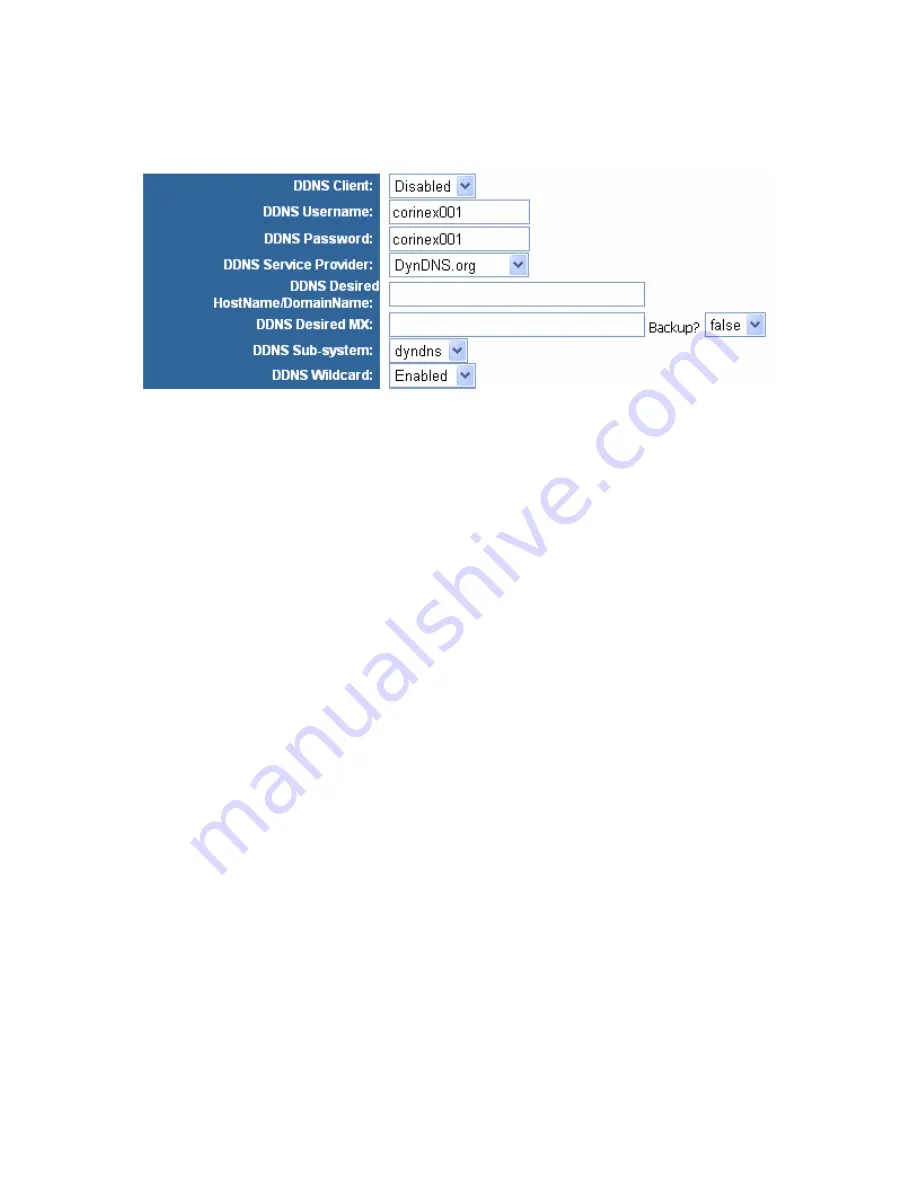
You can
Enable or Disable the DDNS Service by selecting from drop
down menu.
DDNS Username
- Enter the User Name for your DDNS account
DDNS Password
- Enter the Password for your DDNS account.
DDNS Service Provider
- From this pull-down menu, enter the DDNS service with
which you have membership.
DDNS Desired Host Name/Domain Name
–Enter the DDNS URL address assigned by
the DDNS service.
DDNS Desired MX
– The DDNS server system also supports MX records. These can
be used for pointing incoming mail to your domains (such as john.com) to the proper
mail server.
Note:
The DESTINATION ADDRESS of an MX record MUST be a domain name and
NOT simply an IP address.
You can also
Backup
MX service by selecting
true
(for backup) or
false
(for no backup)
option from the drop down menu.
DDNS Sub-system
- You can choose a subsystem name from
dyndns
,
statdns
, or
custom.
DDNS Wildcard
– Wildcard option (only for DynDNS.org)
Some DDNS servers support the wildcard feature which allows the hostname,
*.yourhost.dyndns.org, to be aliased to the same IP address as yourhost.dyndns.org.
This feature is useful when there are multiple servers inside and you want users to be
able to use things such as www.yourhost.dyndns.org and still reach your hostname.






























