39
Corinex
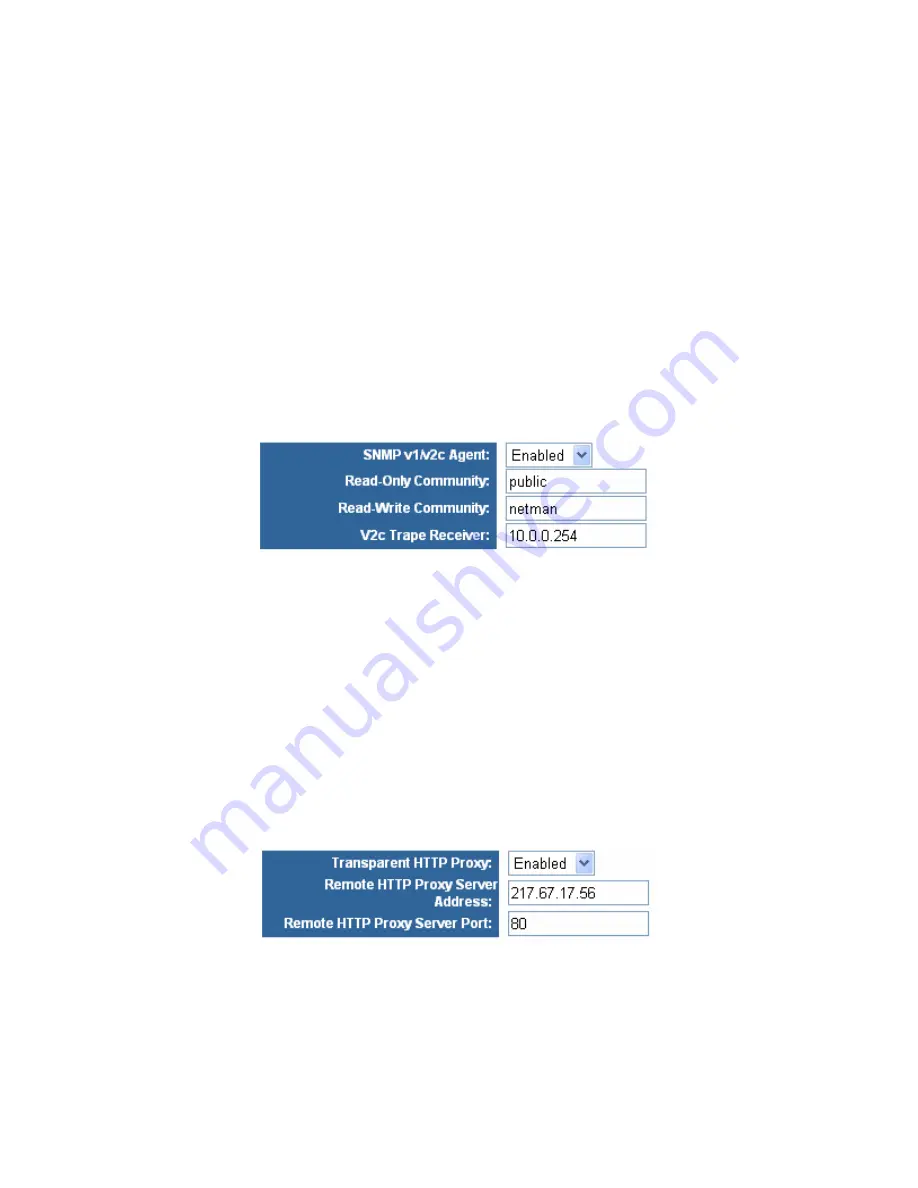
SNMP v1/v2c Agent
allows a SNMP management software (like the Corinex
Open Powerline Management or Corinex Open Management for Hotels software) to
retrieve reports from the networked device. These reports are based upon the defined
objects in the Management Information Base (MIB). The agent queries, reports, and sets
MIB variables based upon directions from the NMS or upon pre-set alarm conditions.
Corinex SNMP v1/v2c will work with the most popular NMS solutions such as HP
OpenView and SunNet Manager. Because the Corinex SNMP v1/v2c Agent is bilingual,
it can communicate with an NMS that is running either SNMP Version 1 or Version 2c.
You can set the SNMP Agent for the SNMP management software to
Enabled
in the
SNMP v1/v2c Agent
drop down menu. Then you can also change the
Read-Only
Community
and
Read-Write Community
strings in the corresponding fields. Default
values are
public
and
netman
, and we are recommending you to change them, as they
are well known and enable others to configure your Router from other computers.
You can also define the trap server IP address in the
V2c Trape Receiver
filed.
HTTP Proxy settings
Using a proxy server leads to reduced bandwidth usage and thus helps keeping the
network-related costs lower. If you want to use Proxy server you must enter the required
parameters in to the following fields.
Transparent HTTP Proxy
- You can
Enable or Disable the HTTP Proxy by selecting
from drop down menu.
Remote HTTP Proxy Server Address
- Enter the Remote HTTP Proxy Server IP
address in this field.
Remote HTTP Proxy Server Port
– Enter the number of the HTTP proxy server port
DDNS Settings
The Router offers a Dynamic Domain Name System (DDNS) feature. DDNS lets you
assign a fixed host and domain name to a dynamic Internet IP address. It is useful when
you are hosting your own website, FTP server, or other server behind the Router. To
















































