Configuring Firewall
43
3.
Select
Applications, Pinholes and DMZ
; a page opens showing hosted applications.
4.
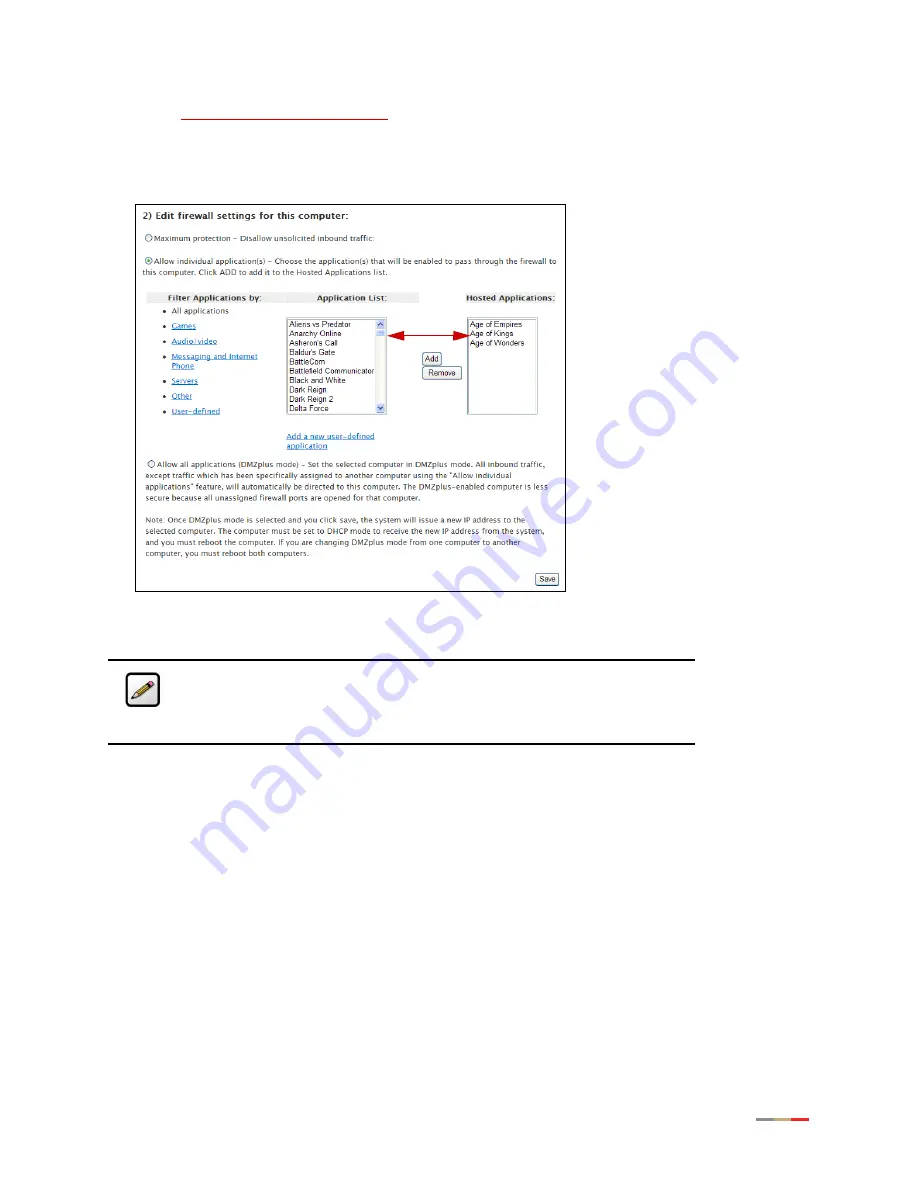
Select the hosting computer if you do not see the pinhole you want to remove in the list.
5.
Scroll to the
Edit firewall settings for this computer
pane.
6.
Select the application(s) you want to remove from the
Hosted Applications
panel, click
Remove
.
7.
Click
Save
; a message appears informing you the status. The application(s) you selected is removed
from the
Hosted Applications
panel and returned to the
Application List
panel.
Defining a New Application Profile
An application profile configures your system’s firewall to pass through application-specific data. You can
define an application profile that is not included in the
Application List
. This feature is typically used if the
application for which you would like to pass through data to a given computer is new or has been recently
updated to a new version.
Note:
To select multiple applications, hold down the [Shift] or [Ctrl] keys
while making your selections. Using the [Shift] key lets you make your
selections in a contiguous order while the [Ctrl] key selects the groups in a
random order.
Содержание i38HG
Страница 1: ...Release 1 0 iNID User Guide ...
Страница 12: ...iNID User Guide 8 ...
Страница 26: ...iNID User Guide 22 ...
Страница 42: ...iNID User Guide 38 ...
Страница 60: ...iNID User Guide 56 3 Click Advanced Configuration the following page opens displaying the default settings ...
Страница 72: ...iNID User Guide 68 ...
Страница 82: ...iNID User Guide 78 ...
Страница 98: ...iNID User Guide 94 3 Click Logs the Event Log page opens 4 Click System Log the System Log page opens ...
Страница 101: ...Finding Solutions 97 3 Click Logs the Event Log page opens 4 Click Firewall Log the Firewall Log page opens ...
Страница 104: ...iNID User Guide 100 ...
Страница 108: ...iNID User Guide 104 ...