Chapter 7 Wireless
VSG1435-B101 Series User’s Guide
120
7.9.3.4 Encryption
Wireless networks can use encryption to protect the information that is sent in the
wireless network. Encryption is like a secret code. If you do not know the secret
code, you cannot understand the message.
The types of encryption you can choose depend on the type of authentication.
(See
Section 7.9.3.3 on page 119
for information about this.)
For example, if the wireless network has a RADIUS server, you can choose
WPA
or
WPA2
. If users do not log in to the wireless network, you can choose no
encryption,
Static WEP
,
WPA-PSK
, or
WPA2-PSK
.
Usually, you should set up the strongest encryption that every device in the
wireless network supports. For example, suppose you have a wireless network
with the ZyXEL Device and you do not have a RADIUS server. Therefore, there is
no authentication. Suppose the wireless network has two devices. Device A only
supports WEP, and device B supports WEP and WPA. Therefore, you should set up
Static WEP
in the wireless network.
Note: It is recommended that wireless networks use
WPA-PSK
,
WPA
, or stronger
encryption. The other types of encryption are better than none at all, but it is still
possible for unauthorized wireless devices to figure out the original information
pretty quickly.
When you select
WPA2
or
WPA2-PSK
in your ZyXEL Device, you can also select
an option (
WPA compatible
) to support WPA as well. In this case, if some of the
devices support WPA and some support WPA2, you should set up
WPA2-PSK
or
WPA2
(depending on the type of wireless network login) and select the
WPA
compatible
option in the ZyXEL Device.
Many types of encryption use a key to protect the information in the wireless
network. The longer the key, the stronger the encryption. Every device in the
wireless network must have the same key.
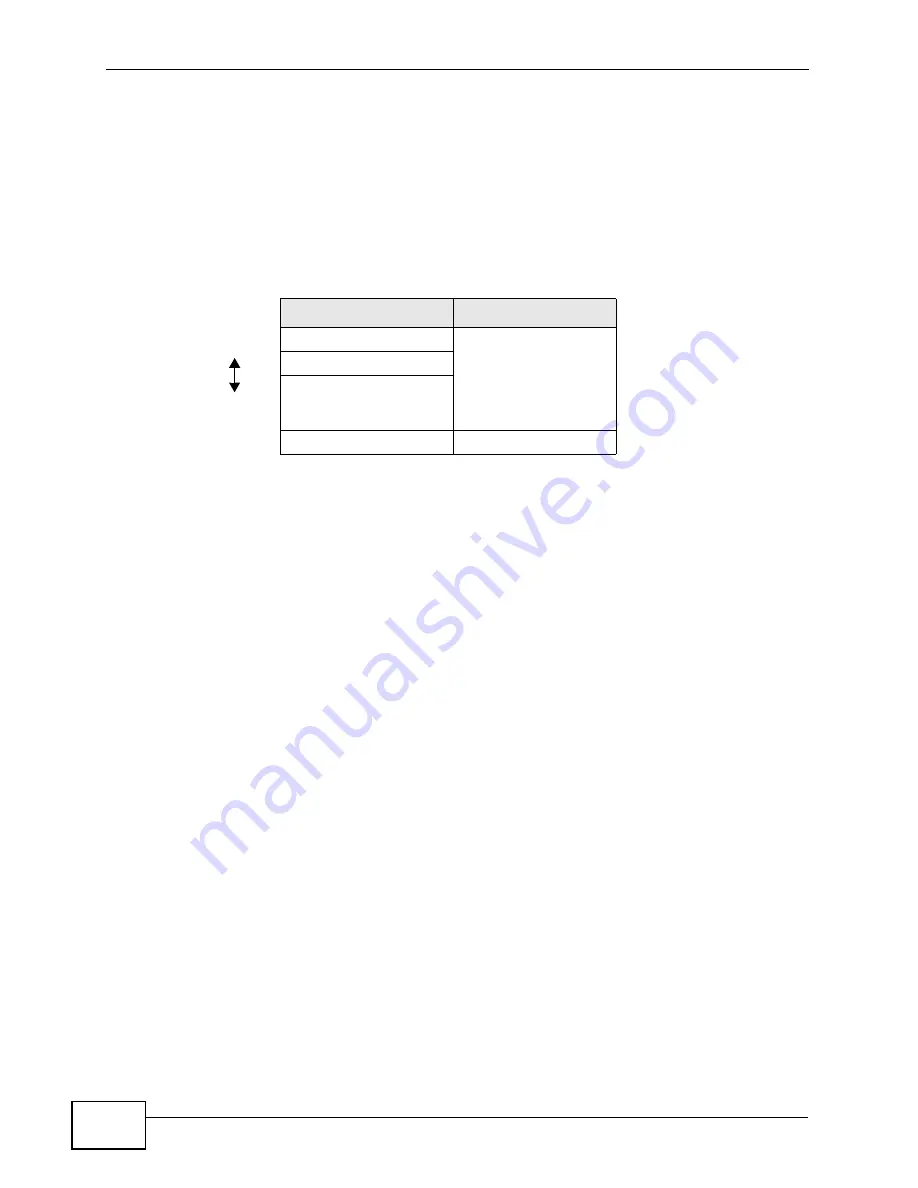
Table 23
Types of Encryption for Each Type of Authentication
NO AUTHENTICATION RADIUS SERVER
Weakest
No Security
WPA
Static WEP
WPA-PSK
Strongest
WPA2-PSK
WPA2
Summary of Contents for VSG1435-B101 - V1.10
Page 2: ......
Page 8: ...Safety Warnings VSG1435 B101 Series User s Guide 8 ...
Page 10: ...Contents Overview VSG1435 B101 Series User s Guide 10 ...
Page 20: ...Table of Contents VSG1435 B101 Series User s Guide 20 ...
Page 21: ...21 PART I User s Guide ...
Page 22: ...22 ...
Page 42: ...Chapter 2 The Web Configurator VSG1435 B101 Series User s Guide 42 ...
Page 71: ...71 PART II Technical Reference ...
Page 72: ...72 ...
Page 78: ...Chapter 5 Network Map and Status Screens VSG1435 B101 Series User s Guide 78 ...
Page 150: ...Chapter 8 Home Networking VSG1435 B101 Series User s Guide 150 ...
Page 154: ...Chapter 9 Static Routing VSG1435 B101 Series User s Guide 154 ...
Page 178: ...Chapter 11 Policy Forwarding VSG1435 B101 Series User s Guide 178 ...
Page 196: ...Chapter 12 Network Address Translation NAT VSG1435 B101 Series User s Guide 196 ...
Page 202: ...Chapter 13 Dynamic DNS Setup VSG1435 B101 Series User s Guide 202 ...
Page 228: ...Chapter 16 Firewall VSG1435 B101 Series User s Guide 228 ...
Page 234: ...Chapter 18 Parental Control VSG1435 B101 Series User s Guide 234 ...
Page 282: ...Chapter 25 Traffic Status VSG1435 B101 Series User s Guide 282 ...
Page 286: ...Chapter 26 IGMP Status VSG1435 B101 Series User s Guide 286 ...
Page 294: ...Chapter 28 Remote Management VSG1435 B101 Series User s Guide 294 ...
Page 298: ...Chapter 29 Time Settings VSG1435 B101 Series User s Guide 298 ...
Page 302: ...Chapter 30 Logs Setting VSG1435 B101 Series User s Guide 302 ...
Page 318: ...Chapter 34 Troubleshooting VSG1435 B101 Series User s Guide 318 ...
Page 348: ...Appendix A Setting up Your Computer s IP Address VSG1435 B101 Series User s Guide 348 ...
Page 358: ...Appendix B IP Addresses and Subnetting VSG1435 B101 Series User s Guide 358 ...
Page 384: ...Appendix D Wireless LANs VSG1435 B101 Series User s Guide 384 ...
















































