Managing MAC Address Table
Security Configurations
User Guide
155
3
Security Configurations
With security configurations of the MAC address table, you can:
■
Configure MAC notification traps
■
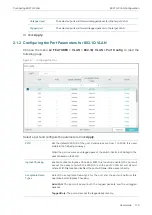
Limit the number of MAC addresses in VLANs
3.1 Using the GUI
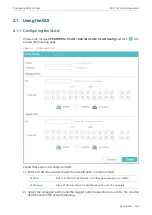
3.1.1 Configuring MAC Notification Traps
Choose the menu
L2 FEATURES > Switching > MAC Address > MAC Notification
to load
the following page.
Figure 3-1
Configuring MAC Notification Traps
Summary of Contents for JetStream T2600G-28TS
Page 264: ...Configuring VLAN VPN Configuration Examples User Guide 235 Figure 4 2 Create VLAN 100 ...
Page 265: ...User Guide 236 Configuring VLAN VPN Configuration Examples Figure 4 3 Create VLAN 200 ...
Page 268: ...Configuring VLAN VPN Configuration Examples User Guide 239 Figure 4 7 Creating VLAN 100 ...
Page 275: ...User Guide 246 Configuring VLAN VPN Configuration Examples Figure 4 11 Create VLAN 100 ...
Page 276: ...Configuring VLAN VPN Configuration Examples User Guide 247 Figure 4 12 Create VLAN 200 ...
Page 277: ...User Guide 248 Configuring VLAN VPN Configuration Examples Figure 4 13 Create VLAN 1050 ...
Page 280: ...Configuring VLAN VPN Configuration Examples User Guide 251 Figure 4 18 Creating VLAN 100 ...
Page 859: ...User Guide 830 Configuring ACL Configuration Example for ACL Figure 3 18 Configuring Rule 3 ...
Page 874: ...Configuring ACL User Guide 845 ...
Page 975: ...Part 33 Monitoring Traffic CHAPTERS 1 Traffic Monitor 2 Appendix Default Parameters ...