57
Chapter 9
Network Security
•
TCP-SYN-FLOOD Attack Filtering
- Enable to prevent the TCP-SYN (Transmission
Control Protocol-Synchronize) flood attack.
Tips:
The level of protection is based on the number of traffic packets. The protection will be triggered immediately
when the number of packets exceeds the preset threshold value (the value can be set on
Advanced
>
System
Tools
>
System Parameters
>
DoS Protection Settings
), and the vicious host will be displayed in the
Blocked
DoS Host List
.
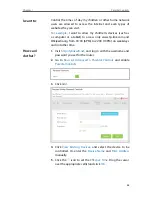
5
If you want to ignore the ping packets from the WAN port, select
Forbid Wan Ping
;
if you want to ignore the ping packets form the LAN port, select
Forbid Lan Ping
.
6
Click
Save
to make the settings effective.
9 2 Access Control
Access Control is used to block or allow specific client devices to access your network
(via wired or wireless) based on a list of blocked devices (Blacklist) or a list of allowed
devices (Whitelist).
Block or allow specific client devices to access my network (via
wired or wireless).
1
Visit
http://tplinkwifi.net
, and log in with the username and
password you set for the router.
2
Go to
Advanced
>
Security
>
Access Control
.
3
Enable
Access Control
.
4
Select the access mode to either block (recommended) or
allow the device(s) in the list.
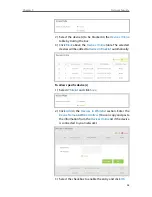
To block specific device(s)
1 ) Select
Blacklist
and click
Save
.
I want to:
How can I
do that?
Summary of Contents for ARCHER C3150
Page 1: ...REV1 0 2 1910011860 Archer C3150 User Guide AC3150 Wireless MU MIMO Gigabit Router ...
Page 49: ...45 Chapter 6 USB Settings Mac 4 Select the printer you share then click Apply Windows ...
Page 58: ...54 Chapter 8 Bandwidth Control Now you and your roommate have an independent bandwidth Done ...
Page 77: ...73 Chapter 11 VPN Server 7 The PPTP VPN connection is created and ready to use ...