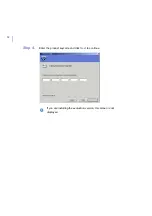
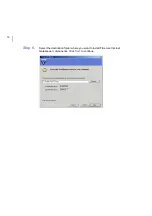
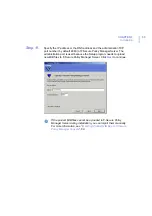
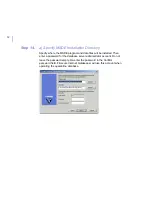
48
The general installation plan is as follows:
1.
Install F- Secure Policy Manager Server and F-Secure Installation
Packages from F- Secure Policy Manager Setup.
For installation instructions, see the chapter
Installing F-Secure Policy
Manager Server
in
F-Secure Policy Manager Administrator’s Guide
.
2.
Install F- Secure Policy Manager Console from F- Secure Policy
Manager Console Setup.
For installation instructions, see the chapter
Installing F-Secure Policy
Manager Console
in
F-Secure Policy Manager Administrator’s Guide
.
3.
Run F- Secure Policy Manager Console for the first time to create the
management key pair and the policy domain. It is recommended to do
this immediately after installing F- Secure Policy Manager Console.
For instructions on how to generate the management key pair, see
the chapter
Installing F-Secure Policy Manager Console
in
F-Secure
Policy Manager Administrator’s Guide
. For instructions on how to
create the policy domain, see section
Managing Domains and Hosts
in
F-Secure Policy Manager Administrator’s Guide
.
4.
Install F- Secure Internet Gatekeeper. For the installation instructions,
go to “
.
5.
Import the product MIB file to F-Secure Policy Manager, if they cannot
be uploaded there during the installation. For more information, see
“
Importing Product MIB files to F-Secure Policy Manager Console
6.
Before you start using the system, check and configure settings for
F-Secure Content Scanner Server, F-Secure Anti-Virus for Internet
Mail, F-Secure Anti-Virus for Internet Gateways and F-Secure
Management Agent. Distribute the policy. For more information, see
“
7.
Make sure the virus and spam definition databases are updated. For
more information, see “
Updating Virus and Spam Definition
.
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...