CHAPTER 10
259
Quarantine Management
10.1
Introduction
You can manage and search quarantined mails with the F-Secure Internet
Gatekeeper Web Console. You can search for quarantined content by
using different search criteria, including the quarantine ID, recipient and
sender address, the time period during which the message was
quarantined, and so on. You can reprocess and delete messages, and
specify storage and automatic deletion times based on the reason for
quarantining the message.
If you have multiple F-Secure Internet Gatekeeper installations, you can
manage the quarantined content on all of them from one single F-Secure
Internet Gatekeeper Web Console. For more information, see “
4: Multiple F-Secure Internet Gatekeeper installations with Centralized
Quarantine Management
and “
Scenario 3: F-Secure Anti-Virus for
Internet Mail for each Sub-domain
.
The quarantine consists of:
quarantine database
quarantine storage.
Quarantine Database
The quarantine database contains information about the quarantined
messages. If there are several F-Secure Internet Gatekeeper installations
in the network, they can either have their own quarantine databases, or
they can use a common quarantine database. An SQL database server is
required for the quarantine database.
The following SQL databases can be used for storing information about
the quarantined content:
Microsoft SQL Server 2000 Desktop Engine (MSDE)
Microsoft SQL Server 2000
Microsoft SQL Server 2005.
MSDE is delivered together with the product. If you want to use another
database (Microsoft SQL Server 2000), you must buy it and get your own
license before you start to deploy F-Secure Internet Gatekeeper.
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
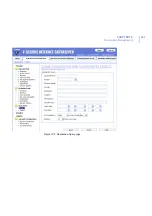
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...