CHAPTER 7
223
Administering F-Secure Content Scanner Server
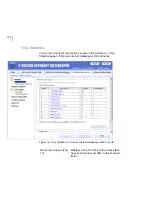
Proxy Configuration
Specify proxy server parameters that Content Scanner Server uses when
it connects to the threat detection center.
Heuristic Scanning - F-Secure Content Scanner
Server checks the message using spam
heuristics.
Trusted Networks
Specify networks and hosts in the mail relay
network which can be trusted not to be operated
by spammers and do not have open relays or
open proxies.
Define the network as a network/netmask pair
(10.1.0.0/255.255.0.0), with the network/nnn
CIDR specification (10.1.0.0/16), or use ‘*’
wildcard to match any number and ‘-’ to define a
range of numbers (172.16.*.1, 172.16.4.10-110).
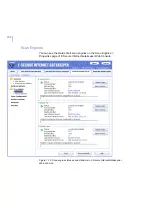
Use Proxy Server
Specify whether F-Secure Content Scanner
Server uses a proxy server when it connects to
the threat detection center.
Proxy Server Address
Specify the address of the proxy server.
Proxy Server Port
Specify the port number of the proxy server.
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...