266
You can select an operation to perform on the messages that were found
in the query:
Click
Reprocess
to scan the currently selected e-mail again, or
click
Reprocess All
to scan all e-mail messages that were found.
For more information, see “
.
Click
Release
to deliver the currently selected e-mail without
further processing, or click
Release All
to deliver all e-mail
messages that were found. For more information, see “
Click
Delete
to delete the currently selected e-mail from the
quarantine, or click
Delete All
to delete all e-mail messages that
were found. For more information, see “
The Query Results page also displays status icons of the e-mails that
were found in the search. If there are reprocessing, release or delete
operations that have not completed yet, the icons indicate which e-mails
are still waiting for the operation:
WARNING: Releasing quarantined content entails a
security risk, because the content is delivered to the
recipient without being scanned.
Icon
E-mail status
Quarantined e-mail. The administrator has not specified any
actions to be taken on this e-mail.
Quarantined e-mail with attachments. The administrator has
not specified any actions to be taken on this e-mail.
This is a quarantined e-mail that the administrator has set to
be released. The release operation has not been completed
yet.
This is a quarantined e-mail that the administrator has set to
be reprocessed. The reprocessing operation has not been
completed yet.
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
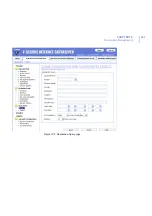
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...