APPENDIX F
357
Advanced Deployment Options
A Note About Deploying Quarantine Management in This
Type of Environment
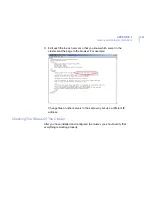
You need to decide whether F-Secure Anti-Virus for Internet Mail
installed in each sub-domain uses its own quarantine database,
or if all F-Secure Anti-Virus for Internet Mail installations use a
common database.
If the F-Secure Anti-Virus for Internet Mail servers are located in
different networks, it is not recommended to use a common
database because of performance reasons.
For more information, see “
Scenario 4: Multiple F-Secure Internet
Gatekeeper installations with Centralized Quarantine
Management
Environment:
There is a F-Secure Anti-Virus for Internet Mail is installed on a
separate computer for each sub-domain. The mail servers of the
sub-domains remain on the original machines.
DNS configuration for sub-domains is changed so that F-Secure
Anti-Virus for Internet Mail host is resolved as
smtp.my.sub*.intranet
and the mail server host is resolved as
pop.my.sub*.intranet
.
The original/upstream Mail Transfer Agent remains on the
smtp.my.intranet
host. It is configured to route inbound mail for
my.sub1.domain
to the
smtp.my.sub1.intranet
host and inbound
mail for
my.sub2.domain
to the
smtp.my.sub2.intranet
host.
Outbound mail is delivered to the mail servers resolved via DNS
MX lookups.
No changes are needed in DNS. DNS MX records point
my.sub1.domain
and
my.sub2.domain
to the
smtp.my.intranet
host (or to the host running the firewall). All inbound mails come
to the Mail Transfer Agent running on the
smtp.my.intranet
host.
No changes are needed in the firewall. Incoming and outgoing
SMTP connections are allowed to/from
smtp.my.intranet
host.
No changes are needed on end-user workstations in sub-domain
networks.
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...