CHAPTER 8
243
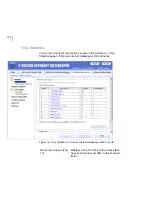
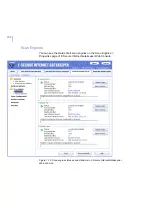
Administering F-Secure Spam Control
When the heuristic spam analysis is
enabled, all messages that the threat
detection engine does not classify as spam
are further analyzed for spam.
When the heuristic spam analysis is
disabled, only the threat detection engine
scans inbound mails for spam.
Heuristic spam analysis slows down the
performance but improves the spam
detection rate.
Spam filtering level
Specify the spam filtering level. Decreasing
the level allows less spam to pass, but more
regular mails may be falsely identified as
spam. Increasing the level allows more
spam to pass, but a smaller number of
regular e-mail messages will be falsely
identified as spam.
For example, if the spam filtering level is set
to 3, more spam is filtered, but also more
regular e-mails may be falsely identified as
spam. If the spam filtering level is set to 7,
more spam will pass undetected, but a
smaller number of regular mails will be
falsely identified as spam.
The allowed values are from 1 to 9.
The spam levels are determined by
calculating points for each e-mail. The spam
scanning involves a large number of different
rules, which give each e-mail different points
depending on the mail content and header
information. These points are then
calculated to a number between 1 and 9,
which defines the likelihood of the message
being spam.
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...