32
Scenario 3: As an Upstream Proxy
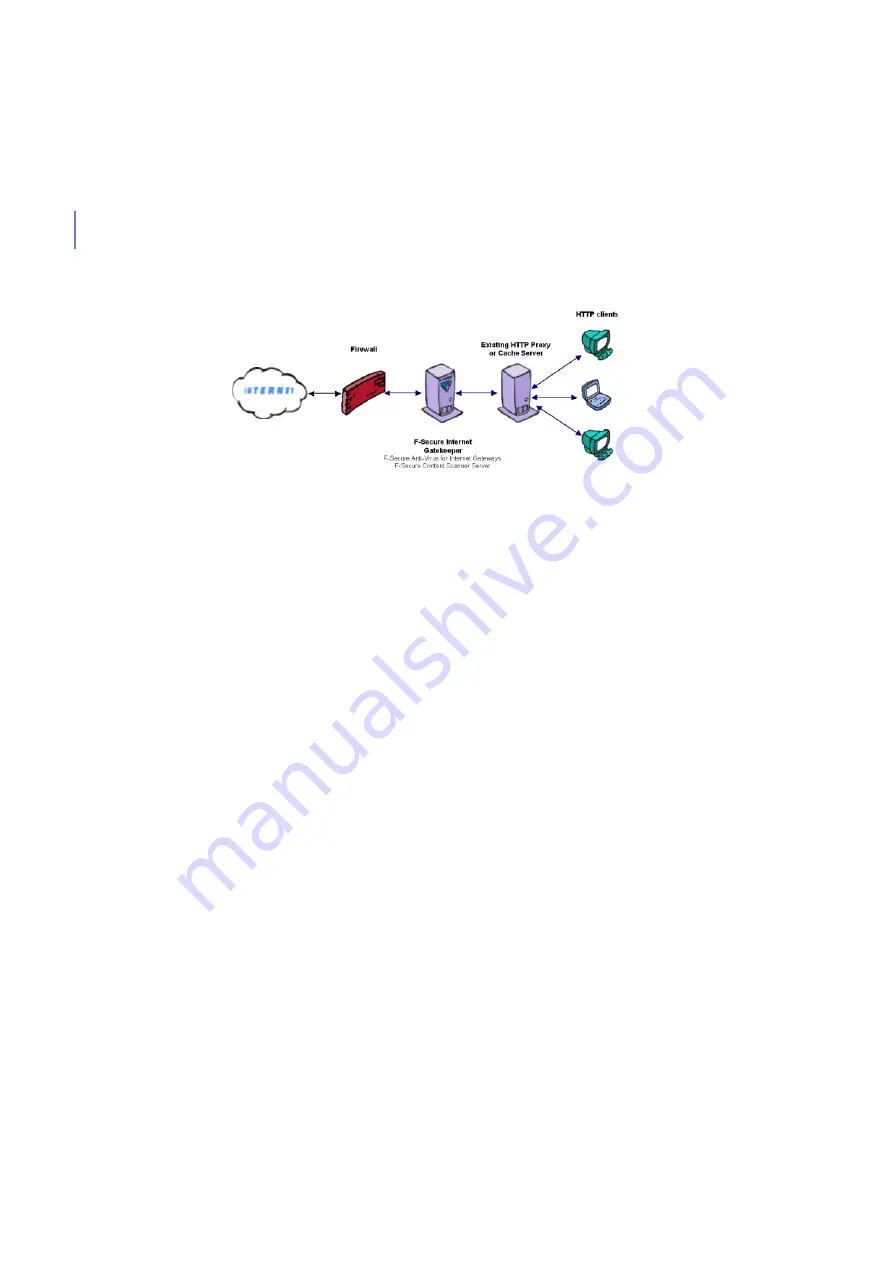
Figure 2-3 F-Secure Anti-Virus for Internet Gateways deployed as an upstream
proxy
Advantages
End-users do not have to change the proxy settings of their web
browsers.
Disadvantages
If virus definition databases are not up-to-date, there is a risk of
malicious code getting to the cache server and HTTP clients
accessing it there.
Configuration on End-User Workstations
Web browser proxy settings do not have to be changed.
F-Secure Anti-Virus for Internet Gateways Configuration
Define the existing HTTP proxy or cache server in the list of hosts
which are allowed to connect to F-Secure Anti-Virus for Internet
Gateways. For more information, see “
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...
















































