Pearl-2 User Guide
Configure network security
Configure network security
Pearl-2 supports 802.1x network security. You can choose the authentication method, upload user
certificates and private key, as well as manage signed CA certificates using the Admin panel. You can also
configure Pearl-2 to use HTTPS.
Topics include:
l
Configure 802.1x network security and manage user certificates
l
Manage CA and self-signed certificates
l
For higher security, we recommend setting admin, operator and viewer-level passwords on Pearl-2, see
.
Configure 802.1x network security and manage user certificates
You can enable 802.1x security and configure the EAP method for Pearl-2 to use for secure network access
using the Admin panel. Supported EAP methods include:
l
PEAP (default)
l
EAP-TLS
l
EAP-TTLS
Important considerations
l
If TLS authentication is used on the network, then you need to get a user certificate and a user private
key from the network administrator and upload those to Pearl-2 as part of this procedure.
l
Before you proceed with this setup, check that the network server's signed CA certificate appears in the
list of CA certificates on Pearl-2 and is valid, see
Manage CA and self-signed certificates
l
If the network server's CA certificate doesn't appear in the list of signed CA certificates and you can't
obtain a valid signed CA certificate for network server authentication, do not check
Verify server's
identity
when performing this setup.
l
Security certificates must be PEM encoded.
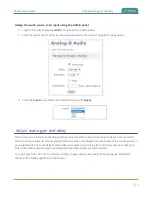
Configure 802.1x and upload the user certificate and user private key using the Admin panel
1. Login to the Admin panel as
admin
.
2. From the Configuration menu, select
Network
. The Network configuration page opens.
3. Under IEEE 802.1x, check
Enabled
and select an
EAP method
: PEAP, EAP-TLS, or EAP-TTLS.
124