11g Wireless Client Bridge/AP
Version 1.36
28
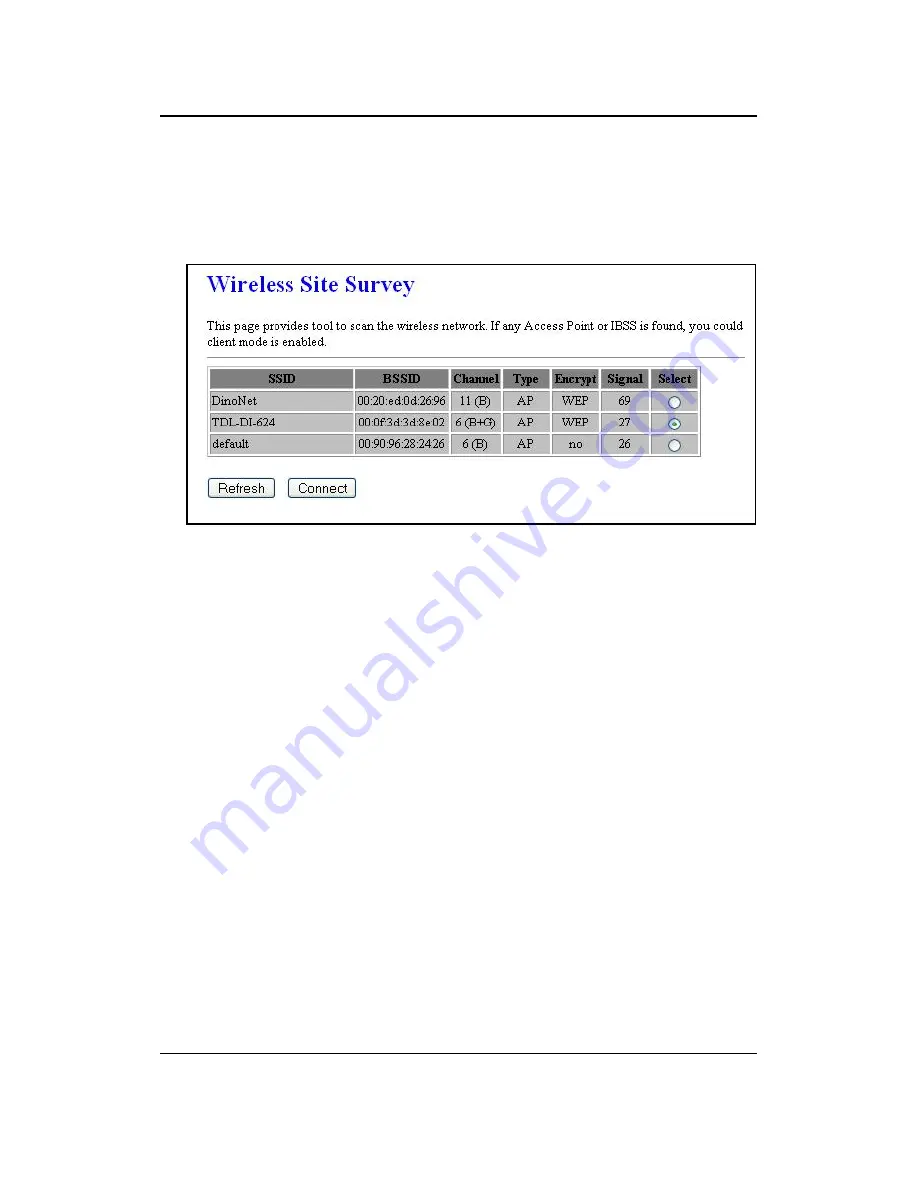
4.4.4 Site Survey
Click
on
the
Site Survey
link under the
Wireless
menu. This page displays the list of
Access Points in the coverage area and allows you to connect to them if you have
the required credentials.
The site survey table lists the following:
o
SSID: This is the unique name of the wireless network.
o
BSSID: This is the MAC address of the Access Point.
o
Channel: This indicates the current channel that the Access Point is
operating on, along with the 802.11 network type (B, G, or B+G).
o
Encrypt: This indicates the encryption type.
o
Signal: This indicates the signal strength of the Access Point.
You may select the radio button of a specific Access Point and then click on the
Conenct
button. If the credentials of this device match that of the Access Point that
you will be connected immediately, if not, you must specify the appropriate
credentials.
You may click on the Refresh button at any time to re-scan the area.






























