DGS-3312SR Gigabit Layer 3 Switch
Enable Method Lists
This window is used to set up Method Lists to promote users with normal level privileges to Administrator level privileges
using authentication methods on the Switch. Once a user acquires normal user level privileges on the Switch, he or she
must be authenticated by a method on the Switch to gain administrator privileges on the Switch, which is defined by the
Administrator. A maximum of eight Enable Method Lists can be implemented on the Switch, one of which is a default
Enable Method List. This default Enable Method List cannot be deleted but can be configured.
The sequence of methods implemented in this command will affect the authentication result. For example, if a user enters a
sequence of methods like TACACS – XTACACS – Local Enable, the Switch will send an authentication request to the
first TACACS host in the server group. If no verification is found, the Switch will send an authentication request to the
second TACACS host in the server group and so on, until the list is exhausted. At that point, the Switch will restart the
same sequence with the following protocol listed, XTACACS. If no authentication takes place using the XTACACS list,
the Local Enable
password set in the Switch is used to authenticate the user.
Successful authentication using any of these methods will give the user an “Admin” privilege.
NOTE:
To set the Local Enable Password, see the next section,
entitled
Local Enable Password.
To view the following table, click
Security > Access Authentication Control > Enable Method Lists
:
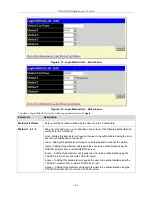
Figure 6- 17. Enable Method List Settings window
To delete an Enable Method List defined by the user, click the
under the
Delete
heading corresponding to the entry
desired to be deleted. To modify an Enable Method List, click on its hyperlinked
Enable Method List Name. To configure
a Method List, click the
Add
button.
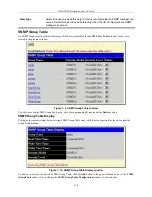
Both actions will result in the same window to configure:
Figure 6- 18. Enable Method List – Add window
149
Summary of Contents for DGS-3312SR
Page 13: ...DGS 3312SR Gigabit Layer 3 Switch xii...
Page 46: ...DGS 3312SR Gigabit Layer 3 Switch Figure 3 14 Stack Information web page 33...
Page 53: ...DGS 3312SR Gigabit Layer 3 Switch 40...
Page 165: ...DGS 3312SR Gigabit Layer 3 Switch Figure 6 22 Enter Network Password dialog box 152...
Page 228: ...DGS 3312SR Gigabit Layer 3 Switch 215...
Page 244: ......