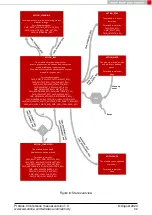
connection) when a connection is initiated. When using this method, the peripheral and
central device output the new generated pass key (see
) when a
connection setup has been initiated. Both, the central and peripheral device request their
hosts to confirm that both keys coincide (see
). If both devices con-
firmed the key, the channel will be opened for data transmission. Otherwise, the connection
will be rejected.
Example: Secured connection with security method "LescNumComp"
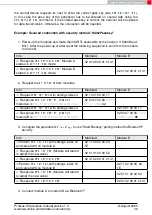
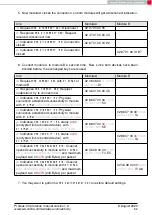
1. Power-up the modules and make their UARTs accessible by the host(s) (115200 Baud,
8n1). After the power-up or after reset the following sequence is sent from the module
to the host.
Info
Module A
Module B
⇐
Response
: Module A
started in
ACTION_IDLE
mode.
02 41 02 00 01 01 41
⇐
Response
: Module B
started in
ACTION_IDLE
mode.
02 41 02 00 01 01 41
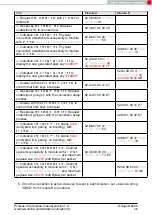
2. Request the
of both modules.
Info
Module A
Module B
⇒
Request
with settings index 4
02 10 01 00 04 17
⇐
Response
of
module A is
0x55 0x00 0x00 0xDA 0x18 0x00
02 50 07 00 00
55 00
00 DA 18 00
C2
⇒
Request
with settings index 4
02 10 01 00 04 17
⇐
Response
of
module B is
0x11 0x00 0x00 0xDA 0x18 0x00
02 50 07 00 00
11 00
00 DA 18 00
86
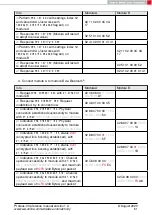
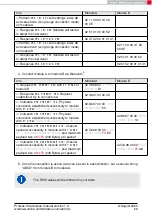
3. Configure the parameter
to use "LescPasskey" pairing method for Bluetooth
®
security.
Proteus-III reference manual version 1.3
© August 2020
www.we-online.com/wireless-connectivity
46