System Config
57
Media Flow Manager Administrator’s Guide
CHAPTER 3 Media Flow Manager Web-Based Interface
System Config > Faults
Configure
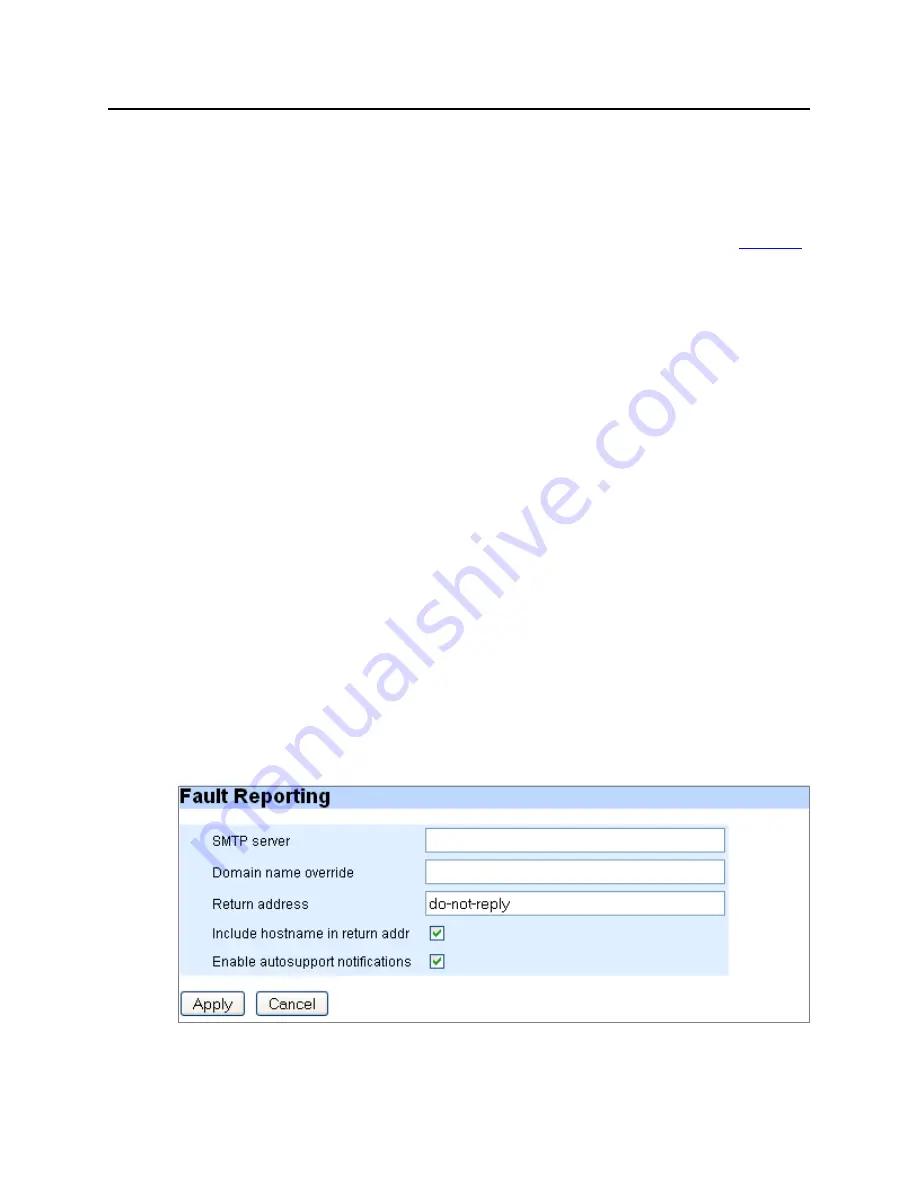
Fault Reporting
options. See
for CLI details.
Fault Reporting
Set SMTP server, Domain name overrides, Return address, and other options. See
Figure 37
,
next.
•
SMTP server
—Use a
hostname
or
IP address
to set the mail relay to use to send
notification emails. Use
no email mailhub
to clear the entry.
•
Domain name override
—Use a
hostname
or
IP address
to set the domain name from
which emails are to appear to come (provided that the return address is not already fully-
qualified). This is used in conjunction with the system hostname to form the full name of
the host from which the email appears to come. The rules are as follows:
a. If an email domain is specified using this command, it is always used. If the
hostname
has any dots in it, everything to the right of the first dot is stripped and the email
domain is appended.
b. Otherwise, if the
hostname
has dots in it, it is used as is.
Otherwise, the currently-active system domain name is used. This can come either from
the resolver configuration, or from state dynamically instantiated by DHCP.
•
Return address
—Set the username or fully-qualified return address from which email
notifications are sent. If the string provided contains an at (@) sign, it is considered fully-
qualified and is used as-is. Otherwise, it is considered just the username, and MFD
appends
@<hostname>.<domain>
. The default is
do-not-reply
, but this can be changed
to
admin
or as desired in case something along the line doesn't like fictitious addresses.
•
Include hostname in return addr
—Include (or do not include by un-checking) the
hostname in the return address for email notifications. This only takes effect if the return
address does not contain an at (@) sign.
•
Enable autosupport notifications
—Enable or disable (by un-checking) the sending of
email to vendor autosupport when certain failures occur.
Click
Apply
to complete Fault notification configuration,
Cancel
to revert to existing
configuration. Click
Save
at the top of the page to make changes persistent across reboots.
Figure 37
System Config > Faults Page Detail (Fault Reporting)
Содержание MEDIA FLOW MANAGER 2.0.2 - ADMINISTRATOR S GUIDE AND CLI
Страница 6: ...Media Flow Manager Administrator s Guide VI Copyright 2010 Juniper Networks Inc...
Страница 12: ...TABLE OF CONTENTS Media Flow Manager Administrator s Guide XII Copyright 2010 Juniper Networks Inc...
Страница 16: ...LIST OF FIGURES XVI Copyright 2010 Juniper Networks Inc...
Страница 152: ...CHAPTER 5 CLI Commands Media Flow Manager Administrator s Guide 152 write Copyright 2010 Juniper Networks Inc...
















































