153
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
The
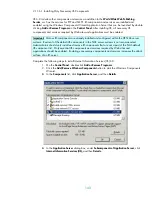
Devices: Restrict floppy access to locally logged-on user only
security option setting determines
whether removable floppy media are accessible to both local and remote users simultaneously.
Enabling this setting allows only the interactively logged-on user to access removable floppy media. If
this policy is enabled, and no one is logged on interactively, the floppy media is accessible over the
network. For CC security compliancy, this value is set to
Enabled
.
Audit: Shut down system immediately if unable to log security audits
Member Server Default
Legacy Client
Enterprise Client
High Security Client
Disabled Enabled Enabled Enabled
This Security Option setting can be configured in Windows Server 2003 at the following location
within the Group Policy Object Editor:
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
The
Audit: Shut down system immediately if unable to log security audits
security option setting
determines whether the system shuts down immediately if it is unable to log security events. The
administrative overhead required to enable this setting in the Legacy Client and Enterprise Client
environments was determined to be too high within NSA security requirements. However, this setting
must be set to
Enabled
for CC security compliancy.
Devices: Unsigned non-driver installation behavior
Member Server Default
Legacy Client
Enterprise Client
High Security Client
Warn but allow
installation
Warn but allow
installation
Warn but allow
installation
Warn but allow
installation
This Security Option setting can be configured in Windows Server 2003 at the following location
within the Group Policy Object Editor:
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
The
Devices: Unsigned non-driver installation behavior
security option setting determines what
happens when an attempt is made to install a non-device driver software that has not been certified.
This option prevents the installation of unsigned non-driver software or warns the administrator that an
unsigned non-driver software is about to be installed. This can prevent installing non-drivers that have
not been certified to run on Windows Server 2003. One potential problem with configuring this
setting to the
Warn but allow installation
value is that unattended installation scripts will fail when
installing unsigned non-drivers.
3.2
Registry Modifications
The following registry modifications or additions are required to meet CC security requirements.
Disable DirectDraw
Key Path: HKLM\SYSTEM\CurrentControlSet\Control\GraphicsDrivers
Format
Value
Key:
DCI
Value
Name:
Timeout
REG_DWORD 0