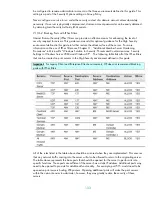
136
Deny access to this computer from the network
Member Server Default
Legacy Client
Enterprise Client
High Security Client
SUPPORT_388945a0 ANONOYMOUS
LOGON; Built-in
Administrator, Guest;
Support_388945a0; all
NONOperating System
service accounts
ANONOYMOUS
LOGON; Built-in
Administrator, Guest;
Support_388945a0; all
NONOperating System
service accounts
ANONOYMOUS
LOGON; Built-in
Administrator, Guest;
Support_388945a0; all
NONOperating System
service accounts
Important:
For all HP NAS server systems, administrators should only deny the Support_388945a0
account.
Note:
ANONOYMOUS LOGON, Built-in Administrator, Support_388945a0, Guest, and all NON-
operating system service accounts are not included in the security template. These accounts and
groups have unique security identifiers (SIDs) for each domain on the network. Therefore, they must be
added manually.
The
Deny access to this computer from the network
setting determines which users are prevented from
accessing a computer over the network. This setting will deny a number of network protocols,
including server message block (SMB)-based protocols, network basic input/output system (NetBIOS),
Common Internet File System (CIFS), Hypertext Transfer Protocol (HTTP), and Component Object
Model Plus (COM+). This setting overrides the
Access this computer from the network
setting when a
user account is subject to both policies. Configuring this user right for other groups could limit the
ability of users to perform delegated administrative tasks on the network. In section 2.8, this guide
recommends including the
Guests
group in the list of users and groups assigned this right to provide
the highest level of security possible. Nevertheless, the IUSR account used for anonymous access to IIS
is by default a member of the
Guests
group. This guide recommends removing the
Guests
group from
the Incremental IIS Group Policy to ensure anonymous access to IIS servers can be configured when
necessary. For these reasons, the
Deny access to this computer from the network
setting is configured
to include
ANONOYMOUS LOGON; Built-in Administrator; Support_388945a0; Guest; all NON-
Operating System service accounts
for IIS servers in all three environments defined in this guide.
2.11.3
Security Options
The Security Options settings for IIS servers in the three environments defined in this guide are
configured via the MSBP. For more information on the MSBP, see section 2.8. The MSBP settings
ensure that all the relevant Security Options are uniformly configured across IIS servers.
2.11.4
Event Log Settings
The Event Log settings for IIS servers in the three environments defined in this guide are configured via
the MSBP. For more information on the MSBP, see section 2.8. The MSBP settings ensure the
appropriate Event Log settings are uniformly configured across IIS servers in an enterprise.
2.11.5
System Services
In order for IIS to add Web server functionality to Microsoft Windows Server 2003, the following
three services must be enabled. The Incremental IIS Group Policy ensures these services are
configured to start automatically.
Note:
The MSBP disables several other IIS related services. FTP, SMTP, and NNTP are some of the
services disabled by the MSBP. The incremental IIS Group Policy must be modified if any of these
services are to be enabled on IIS servers in any of the three environments defined in this guide.