143
restrictive settings are applied. Access to anonymous accounts should be explicitly denied on Web
sites and applications in which anonymous access is not desired. Anonymous access occurs when a
user who has no authenticated credentials accesses system resources. Anonymous accounts include
the built-in
Guest
account, the
Guests
group, and
IIS
Anonymous
accounts. In addition, eliminate any
write access permissions to any users except those that are IIS administrators.
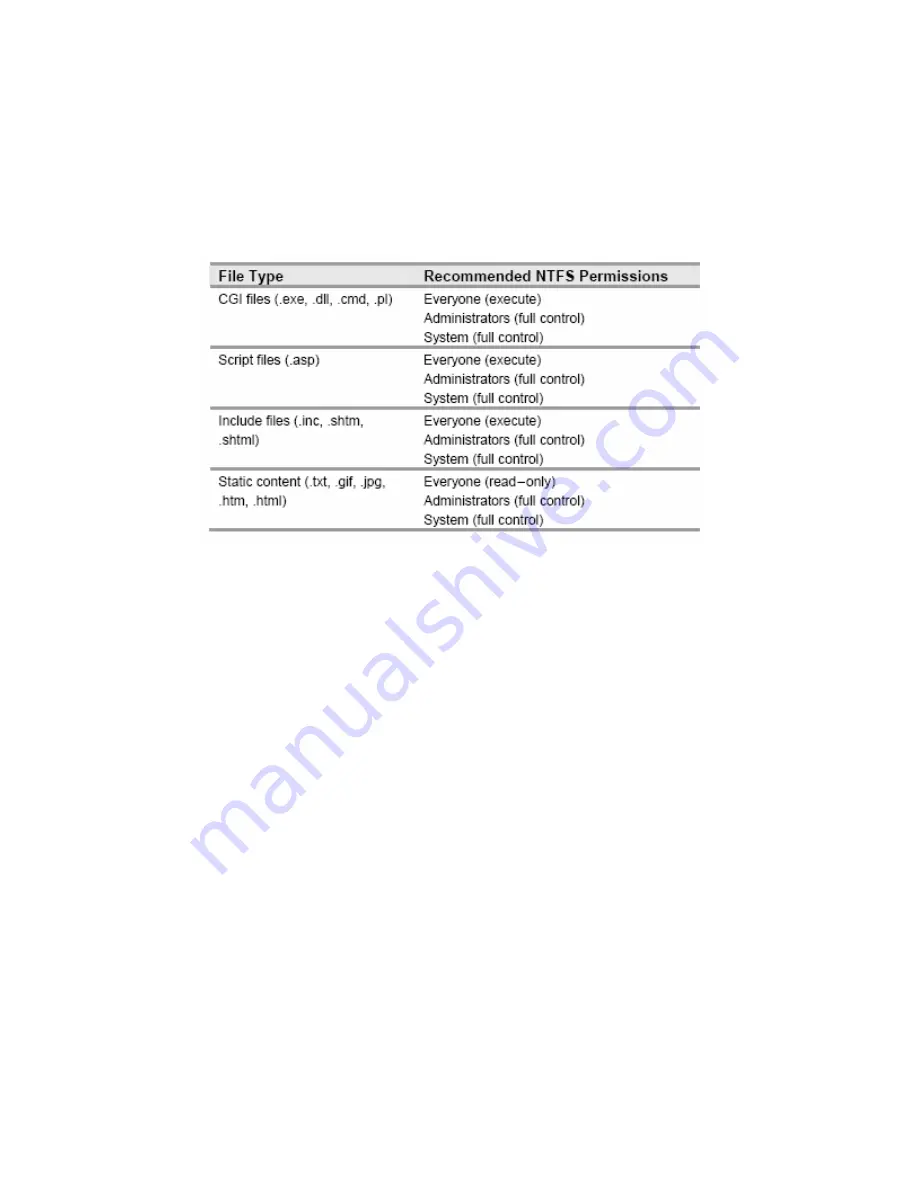
The following table provides some recommendations on the NTFS permissions that should be applied
to the different file types on an IIS server. The different file types can be grouped in separate folders to
simplify the process of applying NTFS permissions.
2.11.6.5
Setting IIS Web Site Permissions
IIS examines Web site permissions to determine the types of action that can occur within a Web site,
such as allowing script source access or directory browsing. Web site permissions should be assigned
to further secure Web sites on IIS servers in the three environments defined in this guide. Web site
permissions can be used in conjunction with NTFS permissions. They can be configured for specific
sites, directories, and files. Unlike NTFS permissions, Web site permissions affect everyone who tries
to access a Web site that runs on an IIS server. Web site permissions can be applied using the IIS
Manager snap-in.
The following table lists the Web site permissions supported by IIS 6.0, and provides a brief
description explaining when to assign any given permission to a Web site.