127
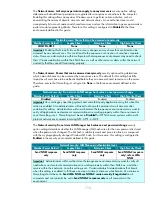
All of the rules listed in the table above should be mirrored when they are implemented. This ensures
that any network traffic coming into the server will also be allowed to return to the originating server.
The table above represents the base ports that should be opened for the server to perform its role-
specific functions. These ports are sufficient if the server has a static IP address. Additional ports may
need to be opened to provide for additional functionality. Opening additional ports will make the file
servers within the network easier to administer, however, they may greatly reduce the security of these
servers.
Important:
These changes could affect performance and should be tested prior to implementing in
production. The exact number of ports that will be opened will depend on the environment as well as
the use and functionality of the server. Client connection times should be monitored. If client response
time or network performance degrade, additional ports may need to be opened.
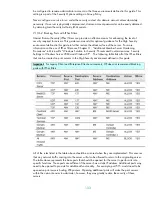
Because of the large amount of interaction between a domain member and the domain controller, in
particular RPC and authentication traffic, all communications are permitted between a file server and
all domain controllers. Traffic could be further limited, but most environments would require the
creation of dozens of additional filters in order for the filters to effectively protect the server. This
would make it very difficult to implement and manage IPSec policies. Similar rules should be created
for each of the domain controllers a file server will interact with. To increase the reliability and
availability of file servers, this will often include adding rules for all domain controllers in the
environment.
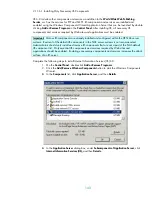
As seen above, if Microsoft Operations Manager (MOM) is implemented in the environment, all
network traffic must be allowed to travel between the server where the IPSec filters are implemented
and the MOM server. This is necessary because of the large amount of interaction between the MOM
server and the OnePoint client-the client application that reports to the MOM console. Other
management packages may have similar requirements. The filter action for the OnePoint client can be
configured to negotiate IPSec with the MOM server if an even greater level of security is desired. This
IPSec policy will effectively block traffic through random high ports, therefore disallowing remote