132
drivers and input/output (I/O) components. Print servers rely on the proper operation of the
Spooler
service. This service must be configured to run in order for a print server to process print jobs
for clients. Using Group Policy to secure and set the startup mode of the
Print Spooler
service grants
access solely to server administrators, and prevents the service from being configured or operated by
unauthorized or malicious users. Group Policy will also prevent administrators from inadvertently
disabling the service. For these reasons, the
Print Spooler
setting is configured to
Automatic
in the
three security environments defined in this guide.
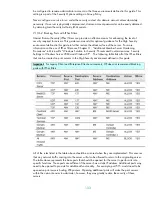
TCP/IP Print Server
Service Name
Member Server
Default
Legacy Client
Enterprise Client High Security Client
LPDSVC Not
installed Disabled Disabled Disabled
Important:
This service must be set to
Automatic
on HP NAS server systems using the Line Printer
Daemon protocol.
The
TCP/IP Print Server
system service enables TCP/IP-based printing using the Line Printer Daemon
protocol. This feature is not required in the baseline server environment. Therefore, this service is
configured to
Disabled
in the three environments defined in this guide.
2.10.6
Additional Security Settings
The security settings applied through the MSBP provide a great deal of enhanced security for print
servers. Nevertheless, there are a few additional considerations that should be taken into account.
These steps cannot be completed via Group Policy and should be performed manually on all print
servers.
2.10.6.1
Securing Well Known Accounts
Microsoft Windows Server. 2003 has a number of built-in user accounts that cannot be deleted but
can be renamed. Two of the most well known built-in accounts in Windows 2003 are
Guest
and
Administrator
. The
Guest
account is disabled by default on member servers and domain controllers.
This setting should not be changed. The built-in
Administrator
account should be renamed and the
description altered to help prevent attackers from compromising a remote server using a well known
account. Many variations of malicious code use the built-in administrator account in an initial attempt
to compromise a server. The value of this configuration change has diminished over the past few
years since the release of attack tools that attempt to break into the server by specifying the security
identifier (SID) of the built-in
Administrator
account to determine its true name. A SID is the value that
uniquely identifies each user, group, computer account, and logon session on a network. It is not
possible to change the SID of this built-in account. Renaming the local administrator account to a
unique name can make it easy for the domain operations groups to monitor attempted attacks against
this account. Complete the following steps to secure well known accounts on the print servers:
1.
Rename the
Administrator
and
Guest
accounts, and then change their passwords to a long and
complex value on every domain and server.
2.
Use different names and passwords on each server. If the same account names and passwords
are used on all domains and servers, an attacker who gains access to one member server will be
able to gain access to all others with the same account name and password.
3.
Change the account descriptions to something other than the defaults to help prevent easy
identification of the accounts.
4.
Record these changes in a secure location.
Note:
The built-in
Administrator
account can be renamed via Group Policy. This setting was not
configured in any of the security templates provided with this guide because administrators should
choose a unique name for their environment. The
Accounts: Rename administrator account
setting can