anonymize traffic between clients and servers across the public Internet so that the client's public IP
address is not present in any server access requests or peer to peer traffic.
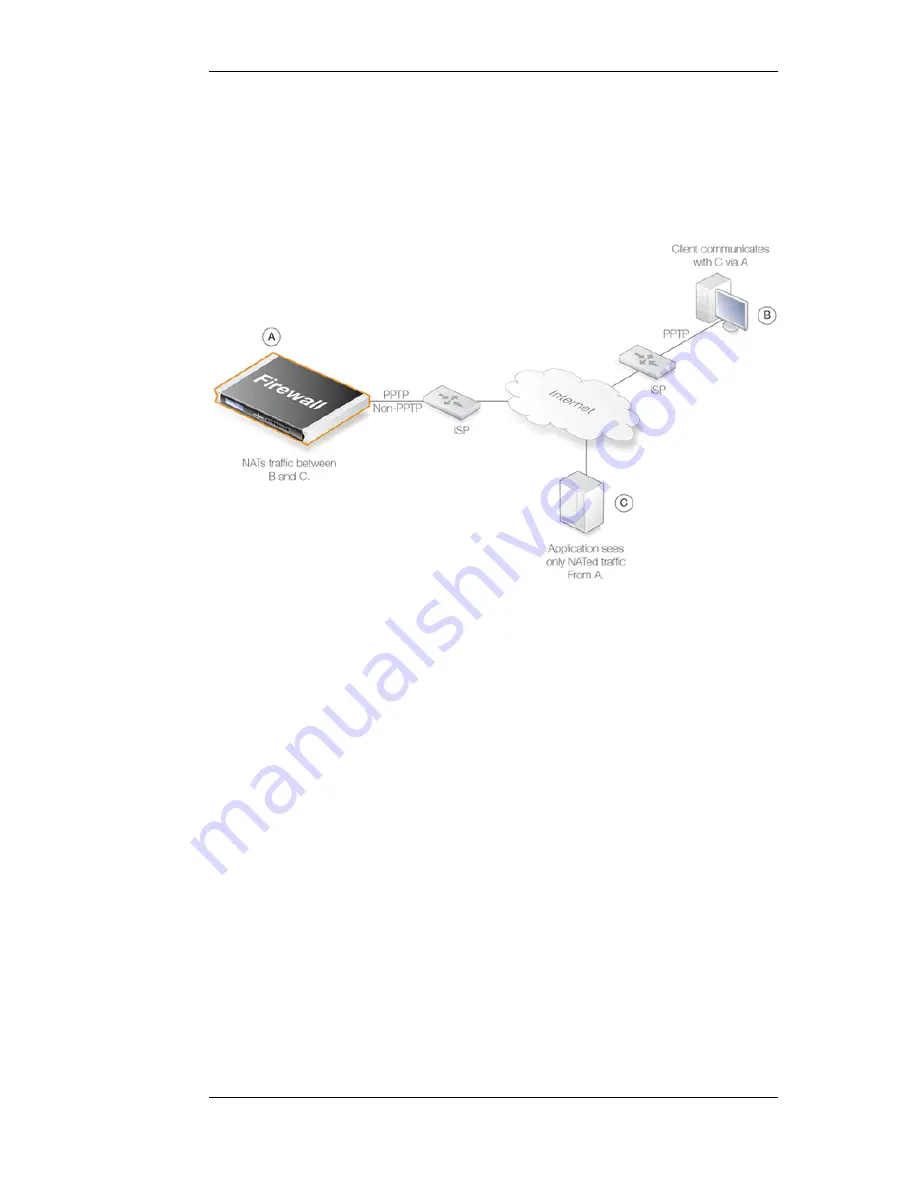
We shall examine the typical case where the NetDefend Firewall acts as a PPTP server and
terminates the PPTP tunnel for PPTP clients. Clients that wish to be anonymous, communicate with
their local ISP using PPTP. The traffic is directed to the anonymizing service provider where a
NetDefend Firewall is installed to act as the PPTP server for the client, terminating the PPTP tunnel.
This arrangement is illustrated in the diagram below.
Figure 7.3. Anonymizing with NAT
NetDefendOS is set up with NAT rules in the IP rule set so it takes communication traffic coming
from the client and NATs it back out onto the Internet. Communication with the client is with the
PPTP protocol but the PPTP tunnel from the client terminates at the firewall. When this traffic is
relayed between the firewall and the Internet, it is no longer encapsulated by PPTP.
When an application, such as a web server, now receives requests from the client it appears as
though they are coming from the anonymizing service provider's external IP address and not the
client's IP. The application therefore sends its responses back to the firewall which relays the traffic
back to the client through the PPTP tunnel. The original IP address of the client is not revealed in
traffic as it is relayed beyond the termination of the PPTP tunnel at the NetDefendOS.
Typically, all traffic passes through the same physical interface and that interface has a single public
IP address. Multiple interfaces could be used if multiple public IP addresses are available. There is
clearly a small processing overhead involved with anonymizing traffic but this need not be an issue
if sufficient hardware resources are employed to perform the anonymizing.
This same technique can also be used with L2TP instead of PPTP connections. Both protocols are
discussed further in Section 9.5.4, “PPTP/L2TP Clients”.
7.2. NAT
Chapter 7. Address Translation
345
Содержание DFL-1600 - Security Appliance
Страница 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27 ...
Страница 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79 ...
Страница 146: ...3 9 DNS Chapter 3 Fundamentals 146 ...
Страница 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227 ...
Страница 241: ...5 4 IP Pools Chapter 5 DHCP Services 241 ...
Страница 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339 ...
Страница 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360 ...
Страница 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382 ...
Страница 386: ... The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386 ...
Страница 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439 ...
Страница 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450 ...
Страница 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488 ...
Страница 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503 ...
Страница 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510 ...
Страница 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533 ...











































