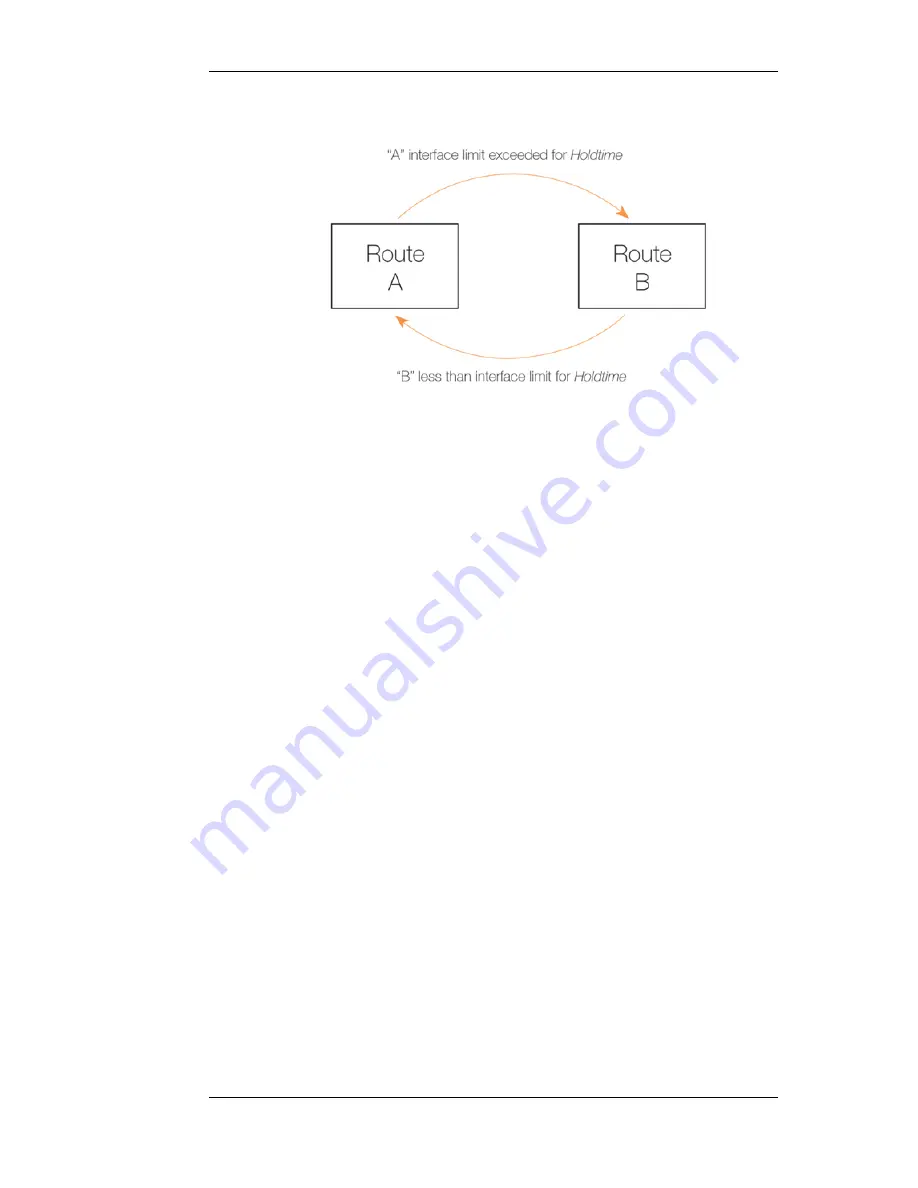
Figure 4.6. The RLB Spillover Algorithm
Spillover Limits are set separately for ingoing and outgoing traffic with only one of these
typically being specified. If both are specified then only one of them needs to be exceeded
continuously for Hold Timer seconds for the next matching route to be chosen. The units of
the limits, such as Mbps, can be selected to simplify specification of the values.
Using Route Metrics with Round Robin
An individual route has a metric associated with it, with the default metric value being zero.
With the Round Robin and the associated Destination algorithms, the metric value can be set
differently on matching routes to create a bias towards the routes with lower metrics. Routes with
lower metrics will be chosen more frequently than those with higher metrics and the proportion of
usage will be based on the relative differences between the metrics of matching routes.
In a scenario with two ISPs, if the requirement is that the bulk of traffic passes through one of the
ISPs then this can be achieved by enabling RLB and setting a low metric on the route to the
favoured ISP. A relatively higher metric is then set on the route to the other ISP.
Using Route Metrics with Spillover
When using the Spillover algorithm, a number of points should be noted regarding metrics and the
way alternative routes are chosen:
•
Route metrics should always be set.
With spillover, NetDefendOS always chooses the route in the matching routes list that has the
lowest metric. The algorithm is not intended to be used with routes having the same metric so
the administrator should set different metrics for all the routes to which spillover applies.
Metrics determine a clear ordering for which route should be chosen next after the interface
traffic limits for the chosen route have been exceeded.
•
There can be many alternative routes.
Several alternative routes can be set up, each with their own interface limits and each with a
different metric. The route with the lowest metric is chosen first and when that route's interface
limits are exceeded, the route with the next highest metric is then chosen.
4.4. Route Load Balancing
Chapter 4. Routing
172
Содержание DFL-1600 - Security Appliance
Страница 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27 ...
Страница 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79 ...
Страница 146: ...3 9 DNS Chapter 3 Fundamentals 146 ...
Страница 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227 ...
Страница 241: ...5 4 IP Pools Chapter 5 DHCP Services 241 ...
Страница 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339 ...
Страница 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360 ...
Страница 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382 ...
Страница 386: ... The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386 ...
Страница 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439 ...
Страница 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450 ...
Страница 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488 ...
Страница 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503 ...
Страница 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510 ...
Страница 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533 ...
















































