9.3 Detection of connections with large data volume transferred
135
cally. With exception of special conditions (testing purposes) it is highly recommended not
to change the default values!
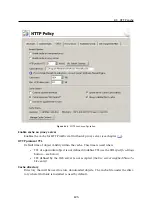
Figure 9.5
Bandwidth Limiter — setting parameters for detection of large data volume transfers
For detailed description of the detection of large data volume transmissions, refer to
chapter
9.3 Detection of connections with large data volume transferred
This chapter provides description of the method used by the
Bandwidth Limiter
module to
detect connections where large data volumes are transmitted. This description is an extra
information which is not necessary for usage of the
Bandwidth Limiter
module.
Network traffic is different for individual services. For example, web browsers usually access
sites by opening one or more connections and using them to transfer certain amount of data
(objects included at the page) and then closes the connections. Terminal services (e.g.
Telnet
,
SSH
, etc.) typically use an open connection to transfer small data volumes in longer intervals.
Large data volume transfers typically uses the method where the data flow continuously with
minimal intervals between the transfer impulses.
Two basic parameters are tested in each connection: volume of transferred data and duration
of the longest idle interval. If the specified data volume is reached without the idleness interval
having been thresholded, the connection is considered as a transfer of large data volume and
corresponding limits are applied.
If the idle time exceeds the defined value, the transferred data counter is set to zero and the
process starts anew. This implies that each connection that
once
reaches the defined values is
considered as a large data volume transfer.
The value of the limit for the amount of data transmitted and the minimal idleness period are
configuration parameters of the
Bandwidth Limiter
(see chapter
).
Summary of Contents for KERIO WINROUTE FIREWALL 6
Page 1: ...Kerio WinRoute Firewall 6 Administrator s Guide Kerio Technologies s r o...
Page 157: ...12 3 Content Rating System Kerio Web Filter 157 Figure 12 7 Kerio Web Filter rule...
Page 247: ...19 4 Alerts 247 Figure 19 14 Details of a selected event...
Page 330: ...Chapter 23 Kerio VPN 330 Figure 23 55 The Paris filial office VPN server configuration...
Page 368: ...368...