Chapter 23
Kerio VPN
312
To provide correct forwarding of DNS requests from a
WinRoute
host, it is necessary to
use an IP address of a network device belonging to the host as the primary DNS server. As
a secondary DNS server, a server where DNS requests addressed to other domains will be
forwarded must be specified (typically the ISP’s DNS server).
Note:
For proper functionality of DNS, the DNS database must include records for hosts
in a corresponding local network. To achieve this, save DNS names and IP addresses of
local hosts into the
hosts
file (if they use IP addresses) or enable cooperation of the
DNS
module with the DHCP server (in case that IP addresses are assigned dynamically to these
hosts). For details, see chapter
4.
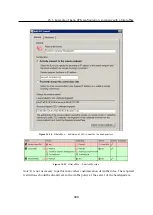
In the
Interfaces
section, allow the VPN server and set its SSL certificate if necessary. Note
the fingerprint of the server’s certificate for later use (it will be required for configuration
of the VPN tunnels in the other filials).
Check whether the automatically selected VPN subnet does not collide with any local sub-
net in any filial and select another free subnet if necessary.
Note:
With respect to the complexity of this VPN configuration, it is recommended to
reserve three free subnets in advance that can later be assigned to individual VPN servers.
5.
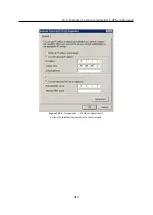
Define the VPN tunnel to one of the remote networks. The passive endpoint of the tunnel
must be created at a server with fixed public IP address. Only active endpoints of VPN
tunnels can be created at servers with dynamic IP address.
Set routing (define custom routes) for the tunnel. Select the
Use custom routes only
option
and specify all subnets of the remote network in the custom routes list.
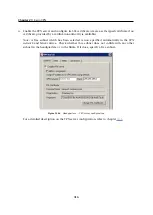
If the remote endpoint of the tunnel has already been defined, check whether the tunnel
was created. If not, refer to the
Error
log, check fingerprints of the certificates and also
availability of the remote server.
6.
Follow the same method to define a tunnel and set routing to the other remote network.
7.
Allow traffic between the local and the remote networks. To allow any traffic, just add the
created VPN tunnels to the
Source
and
Destination
items in the
Local traffic
rule. Access
restrictions options within VPN are described by the example in chapter
.
8.
Test reachability of remote hosts in both remote networks. To perform the test, use the
ping
and
tracert
system commands. Test availability of remote hosts both through IP
addresses and DNS names.
If a remote host is tested through IP address and it does not respond, check configuration
of the traffic rules or/and find out whether the subnets do not collide (i.e. whether the
same subnet is not used at both ends of the tunnel).
If an IP address is tested successfully and an error is reported (
Unknown host
) when a cor-
responding DNS name is tested, then check configuration of the DNS.
Summary of Contents for KERIO WINROUTE FIREWALL 6
Page 1: ...Kerio WinRoute Firewall 6 Administrator s Guide Kerio Technologies s r o...
Page 157: ...12 3 Content Rating System Kerio Web Filter 157 Figure 12 7 Kerio Web Filter rule...
Page 247: ...19 4 Alerts 247 Figure 19 14 Details of a selected event...
Page 330: ...Chapter 23 Kerio VPN 330 Figure 23 55 The Paris filial office VPN server configuration...
Page 368: ...368...