7.3 Definition of Custom Traffic Rules
87
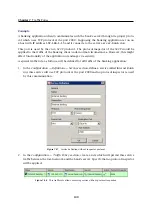
Full cone NAT
For all NAT methods it is possible to set mode of allowing of incoming packets coming from
any address — so called
Full cone NAT
.
If this option is off,
WinRoute
performs so called
Port restricted cone NAT
. In outgoing packets
transferred from the local network to the Internet,
WinRoute
replaces the source IP address of
the particular interface by public address of the firewall (see above). If possible, the original
source port is kept; otherwise, another free source port is assigned. As to incoming traffic,
only packets sent from the same IP address and port from which the outgoing packet was sent
are let in. This translation method guarantees high security — the firewall will not let in any
packet which is not a response to the sent request.
However, many applications (especially applications working with multimedia, Voice over IP
technologies, etc.) use another traffic method where other clients can (with direct connection
established) connect to a port “opened” by an outgoing packet. Therefore,
WinRoute
supports
also the
Full cone NAT
mode where the described restrictions are not applied for incoming
packets. The port then lets in incoming packets with any source IP address and port. This
translation method allows running of applications in the private network that would either
work only partially or they would not work at all.
For example of using of
Full cone NAT
for VoIP applications, refer to chapter
Warning
Use of
Full cone NAT
brings certain security threats — the port opened by outgoing connection
can be accessed without any restrictions being applied. For this reason, it is recommended to
enable
Full cone NAT
only for a specific service (i.e. to create a special rule for this purpose).
By any means do not allow Full cone NAT in the general rule for traffic from the local network
to the Internet
Such rule would significantly decrease security of the local network.
Note:
1.
Older versions of
WinRoute
(to version
6.3.1
incl.) used so called
Symmetric NAT
where
each outgoing connection on the firewall was assigned a new source port from the reserved
range. For this reason, since
6.4.0 WinRoute
includes significantly improved support for
VoIP and multimedia applications than the previous versions even without using special
traffic rules. Both methods have the same security level — they differ only in method of
assigning source ports on the firewall.
2.
The method of IP address translation having been used since version
6.4.0
(i.e.
Port re-
stricted cone NAT
) allows also using of the
IPSec
protocol. Special support for IPSec in-
cluded in older versions of
WinRoute
is not needed any longer.
Typically the
NAT
rule created by the
Traffic policy wizard
— see chapter
Summary of Contents for KERIO WINROUTE FIREWALL 6
Page 1: ...Kerio WinRoute Firewall 6 Administrator s Guide Kerio Technologies s r o...
Page 157: ...12 3 Content Rating System Kerio Web Filter 157 Figure 12 7 Kerio Web Filter rule...
Page 247: ...19 4 Alerts 247 Figure 19 14 Details of a selected event...
Page 330: ...Chapter 23 Kerio VPN 330 Figure 23 55 The Paris filial office VPN server configuration...
Page 368: ...368...