DGS-1510 Series Gigabit Ethernet SmartPro Switch Web UI Reference Guide
199
Action
Select the action that this rule will take here. Options to choose from
are
Permit
and
Deny
.
After selecting the
PCP
option as the
Protocol Type
, the following section will appear.
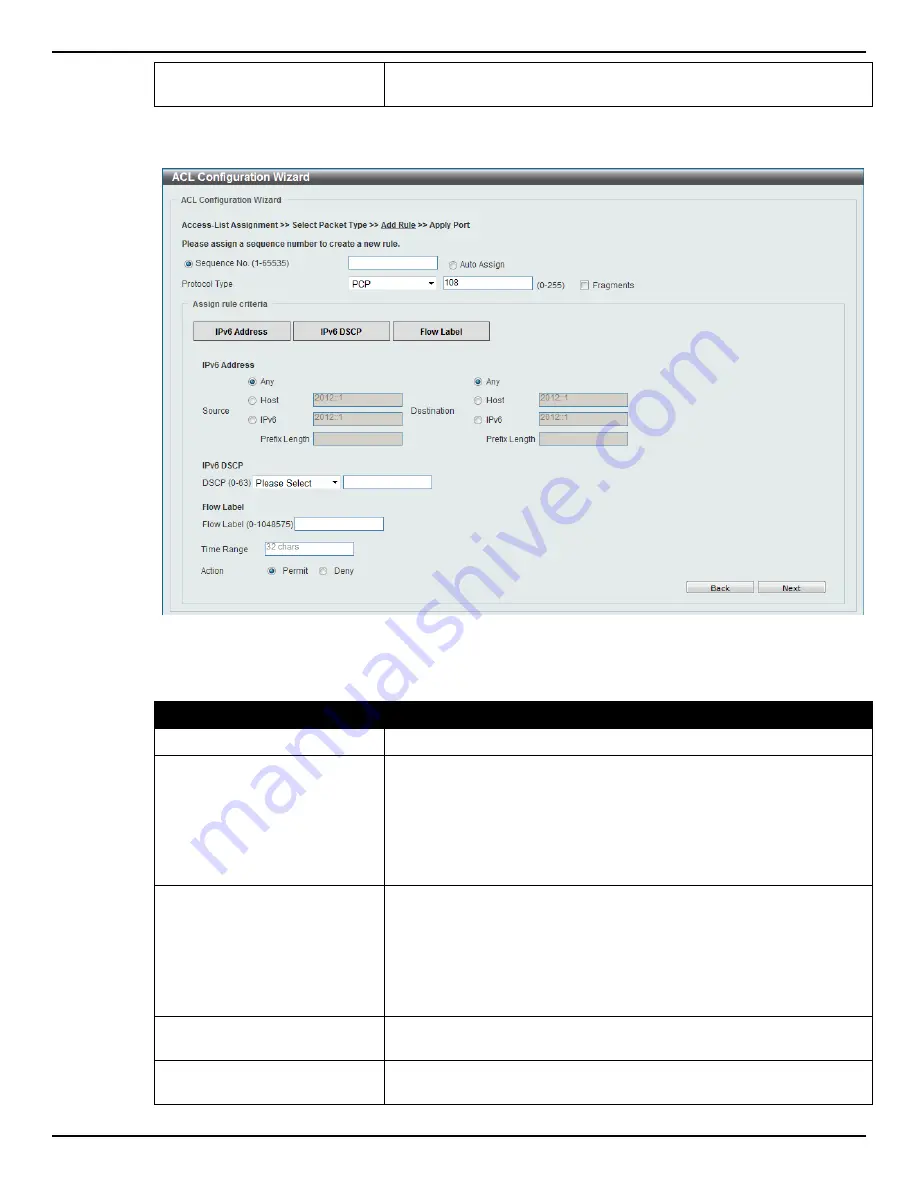
Figure 8-26 ACL Configuration Wizard (Add Rule for IPv6 ACL) PCP window
The
dynamic
fields that can be configured are described below:
Parameter
Description
Fragments
Select the
Fragments
option to include packet fragment filtering.
Source
Select and enter the source information here. Options to choose from
are
Any
,
Host
, and
IPv6
. When the
Any
option is selected, any source
traffic will be evaluated according to the conditions of this rule. When
the
Host
option is selected, enter the source host’s IPv6 address here.
When the
IPv6
option is selected, the
Prefix Length
option will also be
available. Enter the source IPv6 address and prefix length value in the
spaces provided.
Destination
Select and enter the destination information here. Options to choose
from are
Any
,
Host
, and
IPv6
. When the
Any
option is selected, any
destination traffic will be evaluated according to the conditions of this
rule. When the
Host
option is selected, enter the destination host’s
IPv6 address here. When the
IPv6
option is selected, the
Prefix
Length
option will also be available. Enter the destination IPv6
address and prefix length value in the spaces provided.
DSCP
Select or enter the DSCP value used here. This value must be
between 0 and 63.
Flow Label
Enter the flow label value here. This value must be between 0 and
1048575.
Summary of Contents for DGS-1510 Series
Page 1: ...1...






























