You can manage security groups programmatically by using the Amazon Redshift API or the AWS SDKs.
You can also manage the security groups using the Amazon Redshift console without writing any code.
Amazon Redshift applies changes to a security group immediately. So if you have associated the security
group with a cluster, inbound cluster access rules in the updated security group apply immediately.
This section explains how to create a security group, add inbound (ingress) rules, and associate a security
group with a cluster.
Note
If you create a cluster in your own virtual private network (VPC), you cannot use cluster security
groups. Instead, you must use VPC security group to grant inbound access to your cluster in
VPC. For more information about clusters in VPC, see,
Managing Clusters in Virtual Private
Cloud (VPC) (p. 23)
.
Managing Security Groups Using the Console
Topics
•
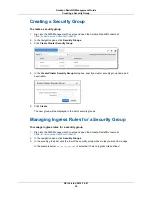
Creating a Security Group (p. 34)
•
Managing Ingress Rules for a Security Group (p. 34)
•
Deleting a Security Group (p. 36)
•
Associating a Security Group with a Cluster (p. 37)
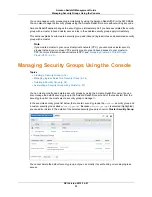
You can create, modify, and delete a security groups by using the Amazon Redshift console. You can
also manage the default security group in the Amazon Redshift console. All of the tasks start from the
security group list. You must select a security group to manage it.
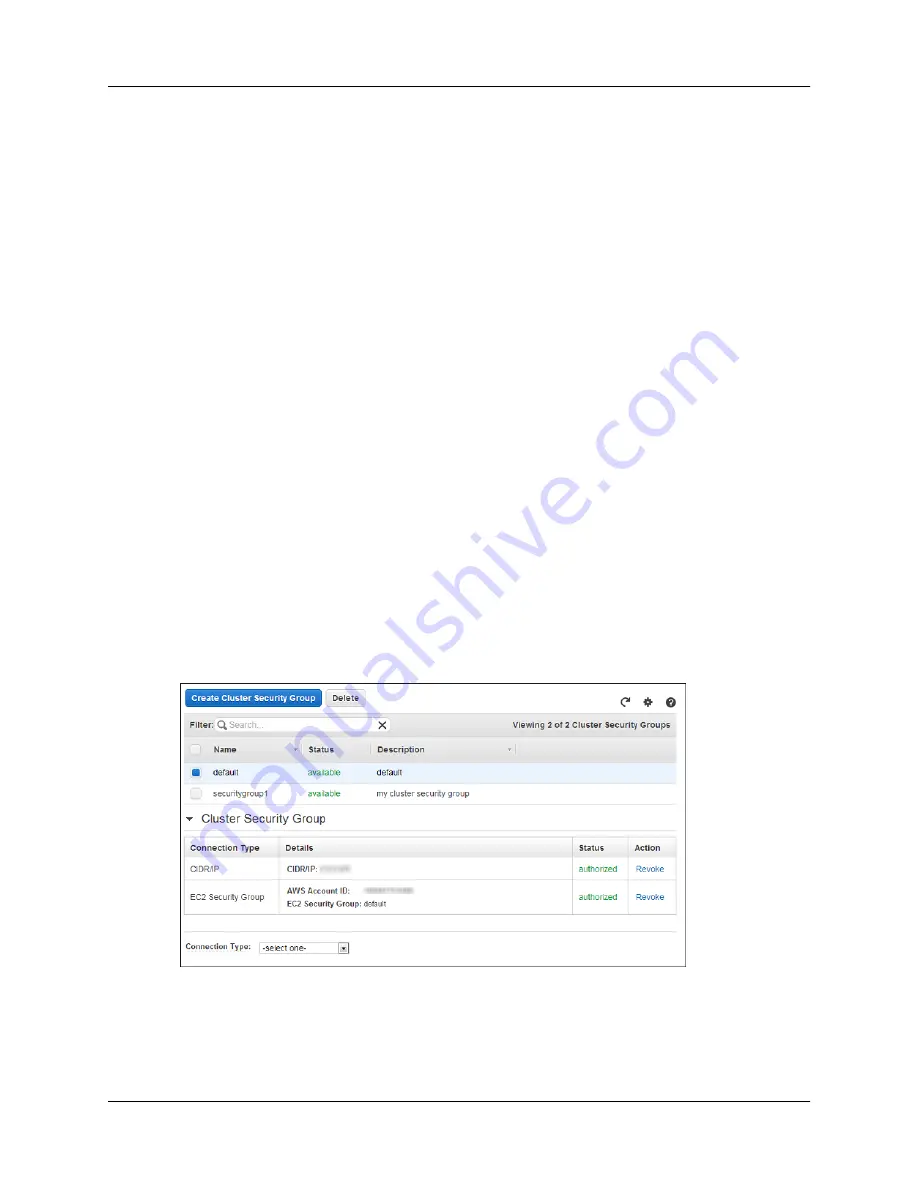
In the example security group list below, there are two security groups, the
default
security group and
a custom security group called
securitygroup1
. Because
securitygroup1
is selected (highlighted),
you can edit or delete it. The details of the selected security group are shown in Cluster Security Group.
You cannot delete the default security group, but you can modify it by authorizing or revoking ingress
access.
API Version 2012-12-01
33
Amazon Redshift Management Guide
Managing Security Groups Using the Console