IAS-2000 v2
User’s Manual
.
129
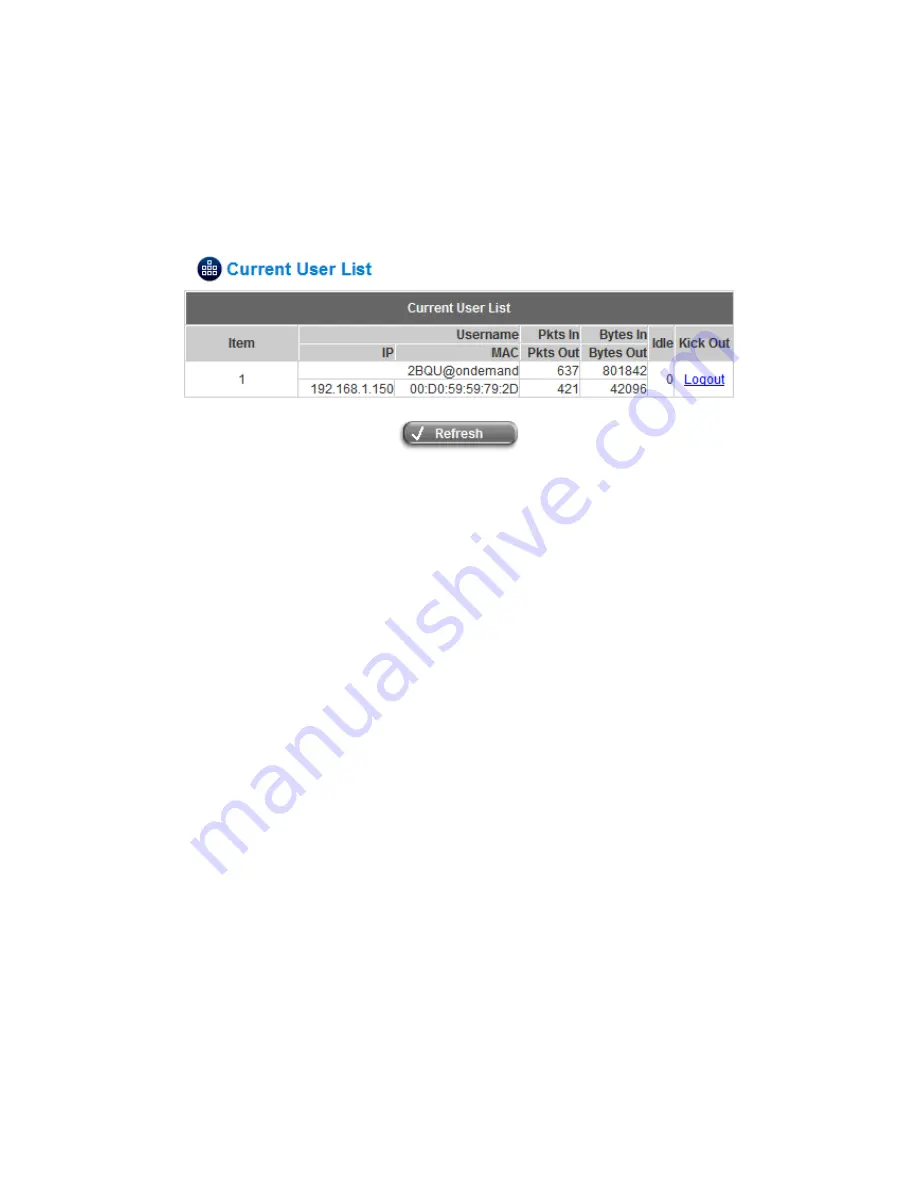
5.5.3 Current Users
In this function, each online user’s information including
Username
,
IP
,
MAC
,
Pkts In
,
Bytes In
,
Pkts Out
,
Bytes
Out,
Idle
and
Kick Out
can be obtained.
Administrator can use this function to force a specific online user to log out.
Just click the hyperlink of
Kick Out
next to the online user’s name to logout that particular user. Click
Refresh
to
renew the Current User List.
Summary of Contents for IAS-2000 V2
Page 1: ...IAS 2000 v2 Internet Access Gateway User s Manual 1 ...
Page 11: ...IAS 2000 v2 User s Manual 4 ...
Page 59: ...IAS 2000 v2 User s Manual 52 ...
Page 100: ...IAS 2000 v2 User s Manual 93 Bandwidth Choose one bandwidth limit for that particular policy ...
Page 163: ...IAS 2000 v2 User s Manual 156 z For Firefox ...






























