218
C
HAPTER
27: Q
O
S C
ONFIGURATION
Two token buckets are used in this evaluation. Their rates of putting tokens into the
buckets are CIR and PIR respectively, and their sizes are CBS and EBS respectively (the
two buckets are called C bucket and E bucket respectively for short), representing
different permitted burst levels. In each evaluation, you can implement different
regulation policies in different conditions, including “enough tokens in C bucket”,
“insufficient tokens in C bucket but enough tokens in E bucket” and “insufficient
tokens in both C bucket and E bucket”.
TP
The typical application of TP is to supervise the specification of certain traffic into the
network and limit it within a reasonable range, or to punish the extra traffic.
Therefore, the network resources and the interests of the operators are protected. For
example, you can limit HTTP packets within 50% of the network bandwidth. If the
traffic of a certain connection is excess, TP can choose to drop the packets or to reset
the priority of the packets.
TP is widely used in policing the traffic into the network of internet service providers
(ISP).TP can classify the policed traffic and perform pre-defined policing actions
according to different evaluation results. These actions include:
■
Forward: Forward the packet whose evaluation result is “conforming” or mark
DSCP precedence for Diff-Serv packets and then forward them.
■
Drop: Drop the packet whose evaluation result is “nonconforming”.
■
Modify the precedence and forward: Modify the priority of the packets whose
evaluation result is “partly-conforming” and forward them.
■
Enter the next-rank policing: TP can be piled up rank by rank and each rank polices
more detailed objects.
TS
TS is a measure to regulate the output rate of traffic actively. Its typical application is
to control local traffic output based on the TP indexes of downstream network nodes.
The major difference between TS and TP is that the packets to be dropped in TP are
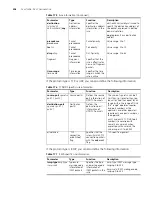
cached in TS—usually in buffers or queues, as shown in Figure 68. When there are
enough tokens in the token bucket, the cached packets are sent out evenly. Another
difference between TP and TS is that TS may increase the delay while TP hardly
increases the delay.
Figure 68
Diagram for TS
Packets sent via this
interface
Continue to send
Token bucket
Put tokens into the bucket at the set rate
Classify
Drop
Queue
Summary of Contents for 4200G 12-Port
Page 10: ...8 CONTENTS...
Page 14: ...4 ABOUT THIS GUIDE...
Page 46: ...32 CHAPTER 5 LOGGING IN THROUGH WEB BASED NETWORK MANAGEMENT SYSTEM...
Page 48: ...34 CHAPTER 6 LOGGING IN THROUGH NMS...
Page 60: ...46 CHAPTER 9 VLAN CONFIGURATION...
Page 64: ...50 CHAPTER 10 MANAGEMENT VLAN CONFIGURATION...
Page 80: ...66 CHAPTER 13 GVRP CONFIGURATION...
Page 98: ...84 CHAPTER 15 LINK AGGREGATION CONFIGURATION...
Page 112: ...98 CHAPTER 18 MAC ADDRESS TABLE MANAGEMENT...
Page 126: ...112 CHAPTER 19 LOGGING IN THROUGH TELNET...
Page 162: ...148 CHAPTER 20 MSTP CONFIGURATION...
Page 274: ...260 CHAPTER 29 IGMP SNOOPING CONFIGURATION...
Page 276: ...262 CHAPTER 30 ROUTING PORT JOIN TO MULTICAST GROUP CONFIGURATION...
Page 298: ...284 CHAPTER 33 SNMP CONFIGURATION...
Page 304: ...290 CHAPTER 34 RMON CONFIGURATION...
Page 338: ...324 CHAPTER 36 SSH TERMINAL SERVICES...
Page 356: ...342 CHAPTER 38 FTP AND TFTP CONFIGURATION...
Page 365: ...Information Center Configuration Example 351 S4200G terminal logging...
Page 366: ...352 CHAPTER 39 INFORMATION CENTER...
Page 378: ...364 CHAPTER 40 BOOTROM AND HOST SOFTWARE LOADING...
Page 384: ...370 CHAPTER 41 Basic System Configuration and Debugging...
Page 388: ...374 CHAPTER 43 NETWORK CONNECTIVITY TEST...
Page 406: ...392 CHAPTER 45 CONFIGURATION OF NEWLY ADDED CLUSTER FUNCTIONS...