USG20(W)-VPN Series User’s Guide
333
C
H A P T E R
2 1
IPSec VPN
21.1 Virtual Private Networks (VPN) Overview
A virtual private network (VPN) provides secure communications between sites without the expense
of leased site-to-site lines. A secure VPN is a combination of tunneling, encryption, authentication,
access control and auditing. It is used to transport traffic over the Internet or any insecure network
that uses TCP/IP for communication.
IPSec VPN
Internet Protocol Security (IPSec) VPN connects IPSec routers or remote users using IPSec client
software. This standards-based VPN offers flexible solutions for secure data communications across
a public network. IPSec is built around a number of standardized cryptographic techniques to
provide confidentiality, data integrity and authentication at the IP layer. The USG can also combine
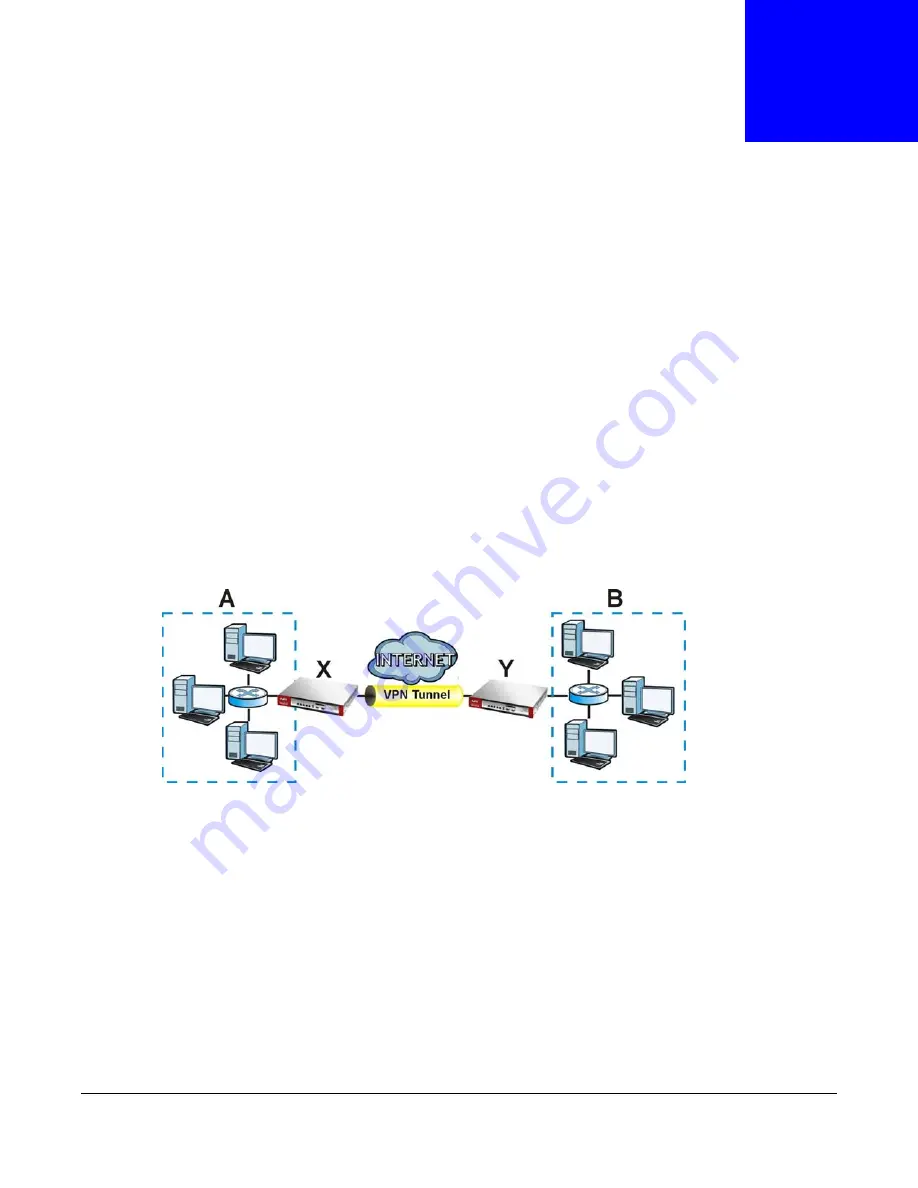
multiple IPSec VPN connections into one secure network. Here local USG
X
uses an IPSec VPN
tunnel to remote (peer) USG
Y
to connect the local (
A
) and remote (
B
) networks.
Figure 221
IPSec VPN Example
Internet Key Exchange (IKE): IKEv1 and IKEv2
The USG supports IKEv1 and IKEv2 for IPv4 and IPv6 traffic. IKE (Internet Key Exchange) is a
protocol used in setting up security associations that allows two parties to send data securely.
IKE uses certificates or pre-shared keys for authentication and a Diffie–Hellman key exchange to
set up a shared session secret from which encryption keys are derived. A security policy for each
peer must be manually created.
IPSec VPN consists of two phases: Phase 1 and Phase 2. Phase 1's purpose is to establish a secure
authenticated communication channel by using the Diffie–Hellman key exchange algorithm to
generate a shared secret key to encrypt IKE communications. This negotiation results in one single
bi-directional ISAKMP Security Association (SA). The authentication can be performed using either
pre-shared key (shared secret), signatures, or public key encryption. Phase 1 operates in either
Содержание ZyWall USG20-VPN
Страница 17: ...17 PART I User s Guide ...
Страница 18: ...18 ...
Страница 99: ...99 PART II Technical Reference ...
Страница 100: ...100 ...
Страница 151: ...Chapter 9 Interfaces USG20 W VPN Series User s Guide 151 Configuration Network Interface Ethernet Edit External Type ...
Страница 152: ...Chapter 9 Interfaces USG20 W VPN Series User s Guide 152 Configuration Network Interface Ethernet Edit External Type ...
Страница 154: ...Chapter 9 Interfaces USG20 W VPN Series User s Guide 154 Configuration Network Interface Ethernet Edit Internal Type ...
Страница 155: ...Chapter 9 Interfaces USG20 W VPN Series User s Guide 155 Figure 121 Configuration Network Interface Ethernet Edit OPT ...
Страница 156: ...Chapter 9 Interfaces USG20 W VPN Series User s Guide 156 Configuration Network Interface Ethernet Edit OPT ...
Страница 170: ...Chapter 9 Interfaces USG20 W VPN Series User s Guide 170 Figure 127 Configuration Network Interface PPP Add ...
Страница 178: ...Chapter 9 Interfaces USG20 W VPN Series User s Guide 178 Figure 129 Configuration Network Interface Cellular Add Edit ...
Страница 194: ...Chapter 9 Interfaces USG20 W VPN Series User s Guide 194 Figure 139 Configuration Network Interface VLAN Add Edit ...
Страница 206: ...Chapter 9 Interfaces USG20 W VPN Series User s Guide 206 Figure 141 Configuration Network Interface Bridge Add Edit ...
Страница 282: ...Chapter 15 UPnP USG20 W VPN Series User s Guide 282 Figure 190 Network Connections My Network Places Properties Example ...
Страница 340: ...Chapter 21 IPSec VPN USG20 W VPN Series User s Guide 340 Figure 226 Configuration VPN IPSec VPN VPN Connection Edit IKE ...
Страница 348: ...Chapter 21 IPSec VPN USG20 W VPN Series User s Guide 348 Figure 228 Configuration VPN IPSec VPN VPN Gateway Add Edit ...
Страница 378: ...Chapter 22 SSL VPN USG20 W VPN Series User s Guide 378 Create a Web Application SSL Application Object ...
Страница 591: ...Chapter 31 Log and Report USG20 W VPN Series User s Guide 591 Figure 418 Configuration Log Report Email Daily Report ...
Страница 659: ...Appendix B Legal Information USG20 W VPN Series User s Guide 659 Environmental Product Declaration ...