-83-
DH Group:
Select the DH (Diffie-Hellman) group to be used in key negotiation phase
1. The DH Group sets the strength of the algorithm in bits. Options include
DH1, DH2 and DH5.
DH1: 768 bits
DH2: 1024 bits
DH3: 1536 bits
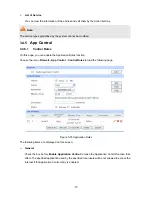
List of IKE Proposal
In this table, you can view the information of IKE Proposals and edit them by the action buttons.
3.5.2 IPsec
IPsec (IP Security) is a set of services and protocols defined by IETF (Internet Engineering Task Force)
to provide high security for IP packets and prevent attacks.
To ensure a secured communication, the two IPsec peers use IPsec protocol to negotiate the data
encryption algorithm and the security protocols for checking the integrity of the transmission data, and
exchange the key to data de-encryption.
IPsec has two important security protocols, AH (Authentication Header) and ESP (Encap
Security Payload). AH is used to guara
the packet has been tampered during
transmission, the receiver will drop this packet when validating the data integrity. ESP is used to check
the encrypted packet is intercepted, the third party
still cannot get the actual information.
3.5.2.1
IPsec Policy
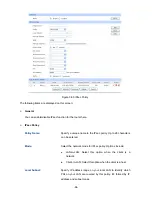
On this page, you can define and edit the IPsec policy.
IPsec Policy
to load the following page.
sulating
ntee the data integrity. If
the data integrity and encrypt the packets. Even if
Choose the menu
VPN
→
IPsec
→