-75-
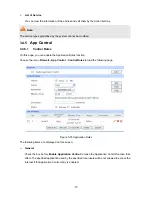
Select the Source IP Range for the entries, including the following
can set the group
on
3.2.1 Group.
ANY: means for any users.
Destination:
Select the Destination IP Range for the entries, including the following
two ways:
IP/MASK: Enter an IP address or subnet mask. ("0.0.0.0/32"
means any IP is acceptable).
ANY: means for any users.
Effective Time:
Specify the time for the entry to take effect.
Description:
Give a description for the entry.
Priority:
Select this option to specify the priority for the added entries. The latest
enabled entry will be displayed at the end of the list by default.
List of Rules
edit them by the Action buttons. The smaller the
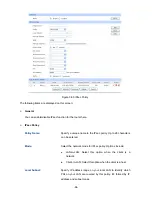
The first entry in Figure 3-53 indicates: The TELNET packets transmitted from the hosts within the
network of 192.168.0.0/24
Tuesday to Saturday.
Source:
three ways:
IP/MASK: Enter an IP address or subnet mask. ("0.0.0.0/32"
means any IP).
Group: Select a predefined group of users. You
You can view the information of the entries and
value is, the higher the priority is.
will be not allowed to pass through the router at 8:00-20:00 from
Note:
●
For the users in the private n
le, the default Policy is Allow.
etwork and not being set access ru
●
To specify all IP addresses, type “0.0.0.0 / 32” in the Policy field.
●
For det
subnet mask, p
ailed setting of
lease refer to
Appendix B FAQ
.