-38-
1)
before
ror function and select the
Ingress & Egress
mode.
apply.
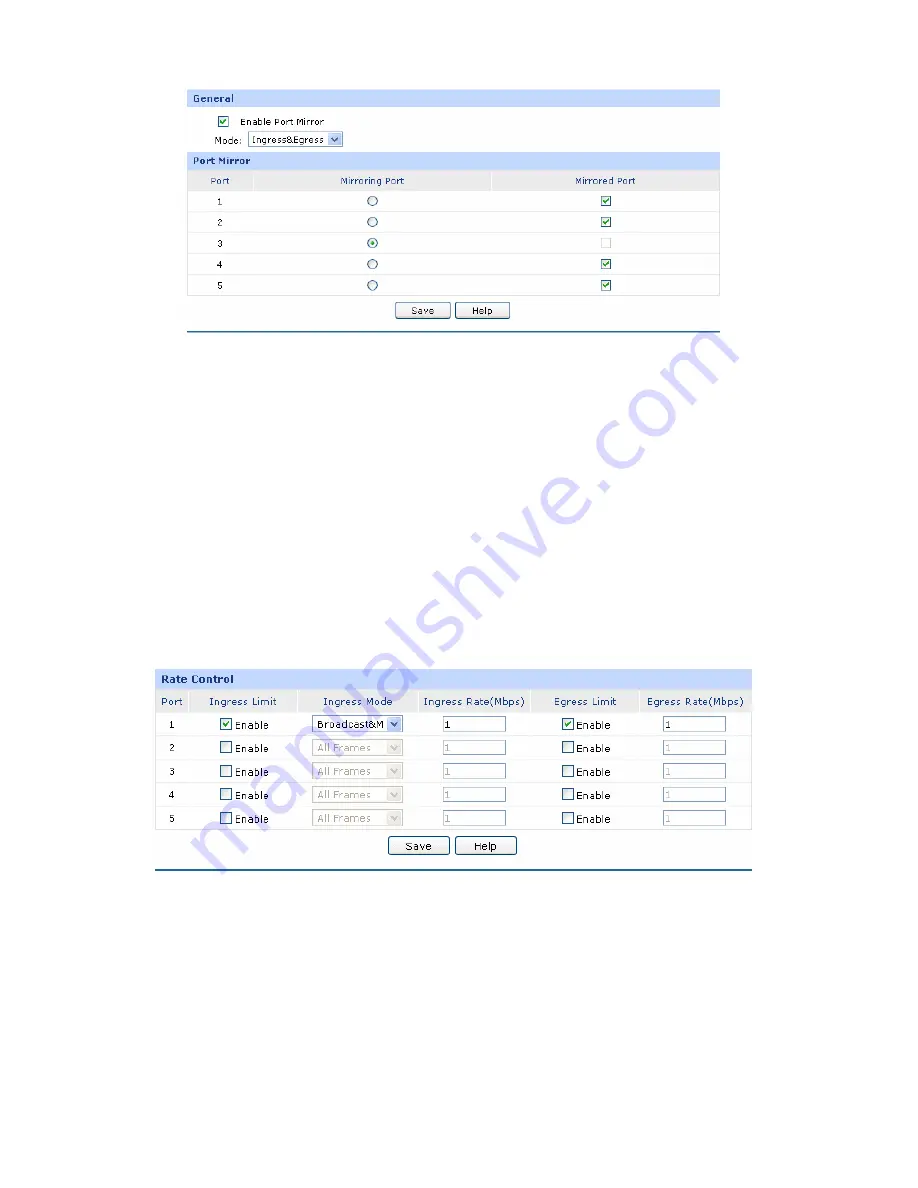
n each port so as to manage your
Choose the menu
Network
→
Switch
→
Rate Control
to load the following page.
Check the box
Enable Port Mirror
to enable the Port Mir
2)
Select Port 3 to be the
Mirroring Port to monitor all the packets of the other ports.
3)
Select all the other ports to be the Mirrored Ports.
4)
Click the <Save> button to
3.1.7.3
Rate Control
On this page, you can control the traffic rate for the specific packets o
network flow.
Figure 3-22 Rate Control
The following items are displayed on this screen:
Rate Control
Port:
Displays the port number.
Ingress Limit:
Specify whether to enable the Ingress Limit feature.






























