-79-
The database refers to all the applications in the application list on the Application Rules page, you can
download the latest database from
http://www.tp-link.com
, Click the <Browse> button and select the
grade>
button to upgrade the database.
ublic network, generally via the
Internet. However, the private network is a logical network without any physical network lines, so it is
called Virtual Private Network.
With the wide application of the Internet, more and more data are needed to be shared through the
Internet. Connecting the local network to the Internet directly, though can allow the data exchange, will
cause the private data to be exposed to all the users on the Internet. The VPN (Virtual Private Network)
technology is developed and used to establish the private network through the public network, which
can guarantee a secured data exchange.
VPN adopts the tunneling technology to establish a private connection between two endpoints. It is a
connection secured by encrypting the data and using point-to-point authentication. The following
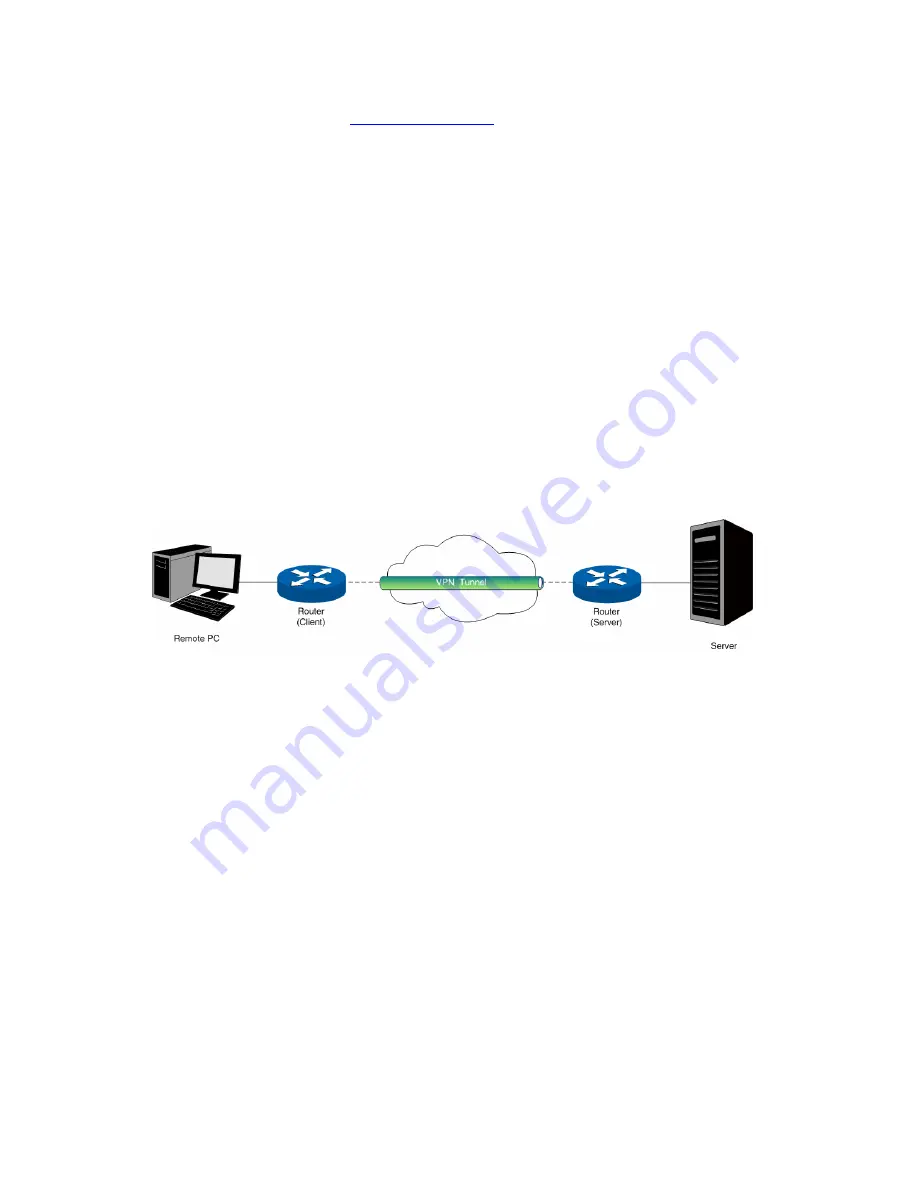
diagram is a typical VPN topology.
file, and then click the
<Up
3.5 VPN
VPN (Virtual Private Network) is a private network established via the p
Figure 3-57 VPN – Network Topology
As the packets are encapsulated and de-encapsulated in the router, the tunneling topology
implemented by encapsulating packets is transparent to users. The tunneling protocols supported by
TL-ER6120 contain Layer 3 IPsec and Layer 2 L2TP/PPTP.
PN, to ensure a secure communication, the two peers should encapsulate and
ackets using the information both known. Therefore the two peers need to
negoti
y for co
Actually IKE is a hybrid prot
t
Security Association and Key Management Protocol), Oakley Key Determination Protocol, and
SKEME Security Key Exchange Protocol. ISAKMP provides a framework for Key Exchange and SA
(Security Association) negotiation. Oakley describes a series of key exchange modes. SKEME
describes another key exchange mode different from those described by Oakley.
IKE consists of two phases. Phase 1 is used to negotiate the parameters, key exchange algorithm and
encryption to establish an ISAKMP SA for securely exchanging more information in Phase 2. During
3.5.1 IKE
In the IPsec V
de-encapsulate the p
ate a security ke
mmunication with IKE (Internet Key Exchange) protocols.
ocol based on three underlying security protocols, ISAKMP (Interne