R-sensors LLC
Bldg. 1, 4, Likhachevsky proezd, Dolgoprudny, 141701, Russia
+7 (498) 744-69-95,
NDAS-N. User Manual.
51
11.2 Module configuration page
The
config
button opens a dedicated page of the NDAS-RT firewall configuration.
A set of rules can be configured for each network connection. That is, for example, the firewall
to protect an Ethernet connection can be configured and the full access for a USB connection and a VPN
tunnel can be left.
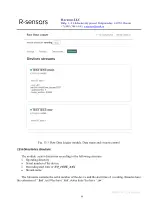
The list of network connections is given in the table below.
Table 11.1. NDAS-RT network connections:
Ethernet (eth0)
Ethernet network
Modem connection (ppp0)
3G modem connection
USB virtual network (usb0) USB virtual network
Wi-Fi station (wlan0)
Wi-Fi connection in the station mode
Wi-Fi access point (tether)
Wi-Fi connection in the access point mode
VPN tunnel (tun0)
VPN tunnel
Software for the NDAS-N data logger and the NDAS-RT multifunction module is identical.
The functions and capabilities described in this chapter for NDAS-RT also refer to the data
logger.
Each rule is based on the principle of whitelisting for incoming connections. In total, there are 3
lists for each connection: the TCP ports list, the UDP ports list, and the IP addresses list. If the whitelist
is disabled, all connections of the appropriate type are allowed for the selected network interface. If the
whitelist is enabled, only connections of the list will be allowed.
To create a new set of rules, click
add rule
, set the required configuration, and click
apply
.
Only one set of rules must match each interface.
Changing the set of rules requires super-user rights so the password for the debian account
will be requested.
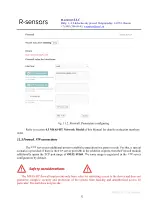
For example, in the screenshot below the TCP and UDP ports whitelists are enabled for the ppp0
interface (modem connection). Connections to ports 8000, 3000, 18000, 21, and 22 are allowed for TCP.
For UDP the list is empty, that is, all UDP connections are prohibited. Since the whitelist for IP addresses
is not enabled, connections from any IP addresses are allowed.