Proroute
GEM
2M
4G
Router
GEM-2M series User Manual
107
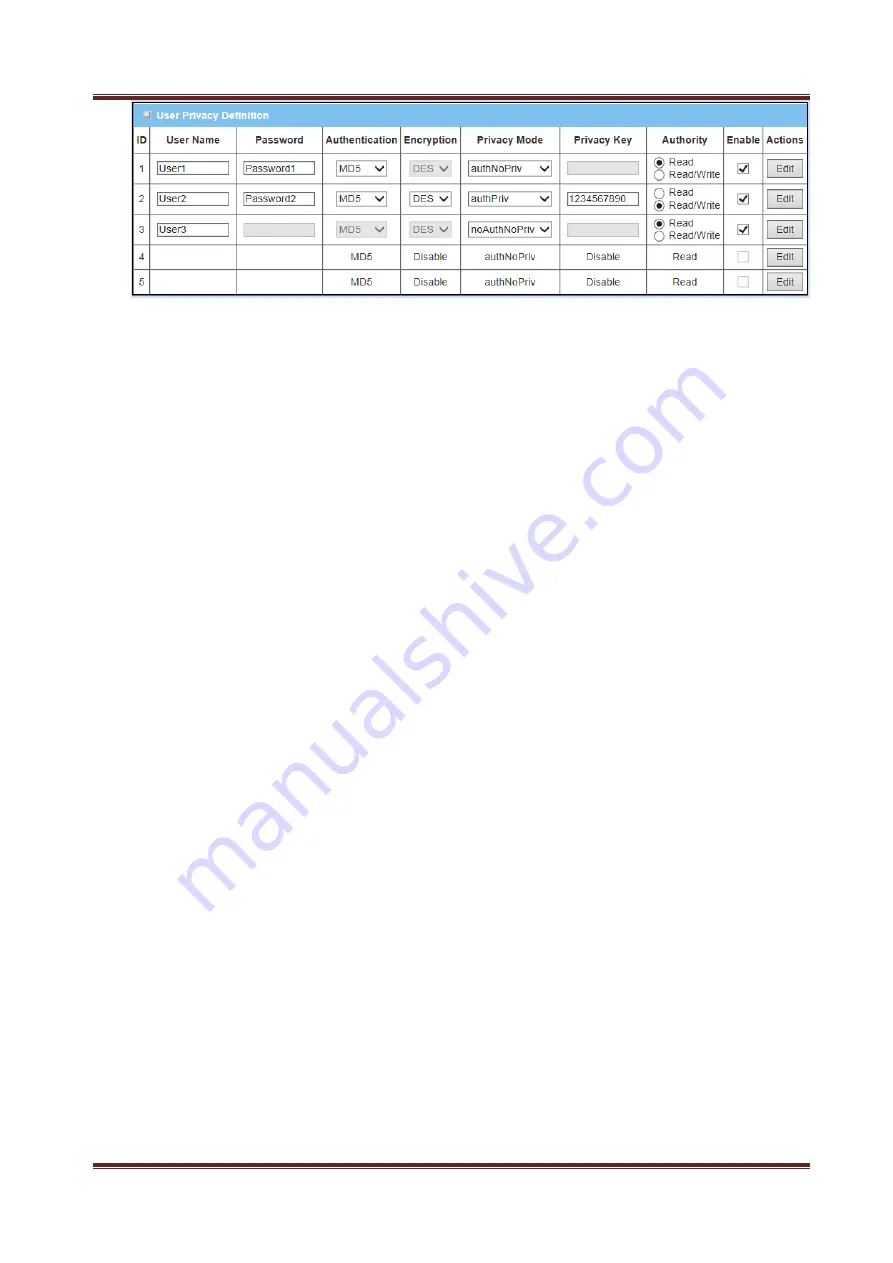
1. User Name
: Input the name for a user.
2. Password & Authentication
: Input the password for a user and choose the
hashing algorithm for authentication. However, they will not be necessary when
you choose the privacy mode to be "noAuthPriv" for the user account.
3. Privacy Mode:
Choose the privacy mode for the specific user. There are three
options, "NoAuthNoPriv", "AuthNoPriv" and "AuthPriv".
4. Privacy Key & Encryption:
Input the privacy key for a user and choose the
encryption algorithm for security.
5. Authority:
Specify the Read or Write authority for the user account.
6. Enable:
To activate the user account by checking the Enable box.
Afterwards, click on “Save” to store your settings or click “Undo” to give up the
changes.
3.2.5.3 Telnet with CLI
A command-line interface (CLI), also known as command-line user interface, console
user interface, and character user interface (CUI), is a means of interacting with a
computer program where the user (or client) issues commands to the program in the
form of successive lines of text (command lines). The interface is usually
implemented with a command line shell, which is a program that accepts commands
as text input and converts commands to appropriate operating system functions.
Programs with command-line interfaces are generally easier to automate via scripting.
The device supports both Telnet and SSH CLI with default service port 23 and 22,
respectively. And it also accepts commands from both LAN and WAN sides.






























