Chapter 3 – RouteFinder Software Operation
Multi-Tech RouteFinder RF650VPN User Guide
129
Generate RSA Key
Here you generate a new pair of keys. The pair of keys consists of a private key and a public key. To be
able to communicate with the other party, you exchange public keys. This exchange can be done via e-
mail. The generation of the pair of keys can take up to 15 minutes, depending on the key length and other
variables.
Note: When generating a new RSA key, all VPN connections that use the old RSA key will become
inoperable. We recommend using RSA keys with a minimum length of 1536 Bits.
To generate a new RSA key, at VPN|IPSec RSA key|Generate RSA key perform the following steps.
1.
Select the desired Keylength in bits from the Keylength in bits dropdown list. The Keylength
options are 512 bits (default), 1024 bits, 1536 bits, 2048 bits, or 2560 bits.
2.
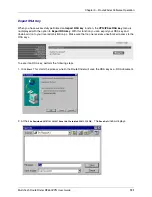
Click Start. A Logfile window opens with information about the ongoing key generation process.
3.
By opening the
Live-Log
window you can watch the RSA key creation process. The
Public Key xxxx Bits
displayed in the
LiveLog
window is the transmission state of the private part of your RSA key to the
VPN counterpart.