Use
To
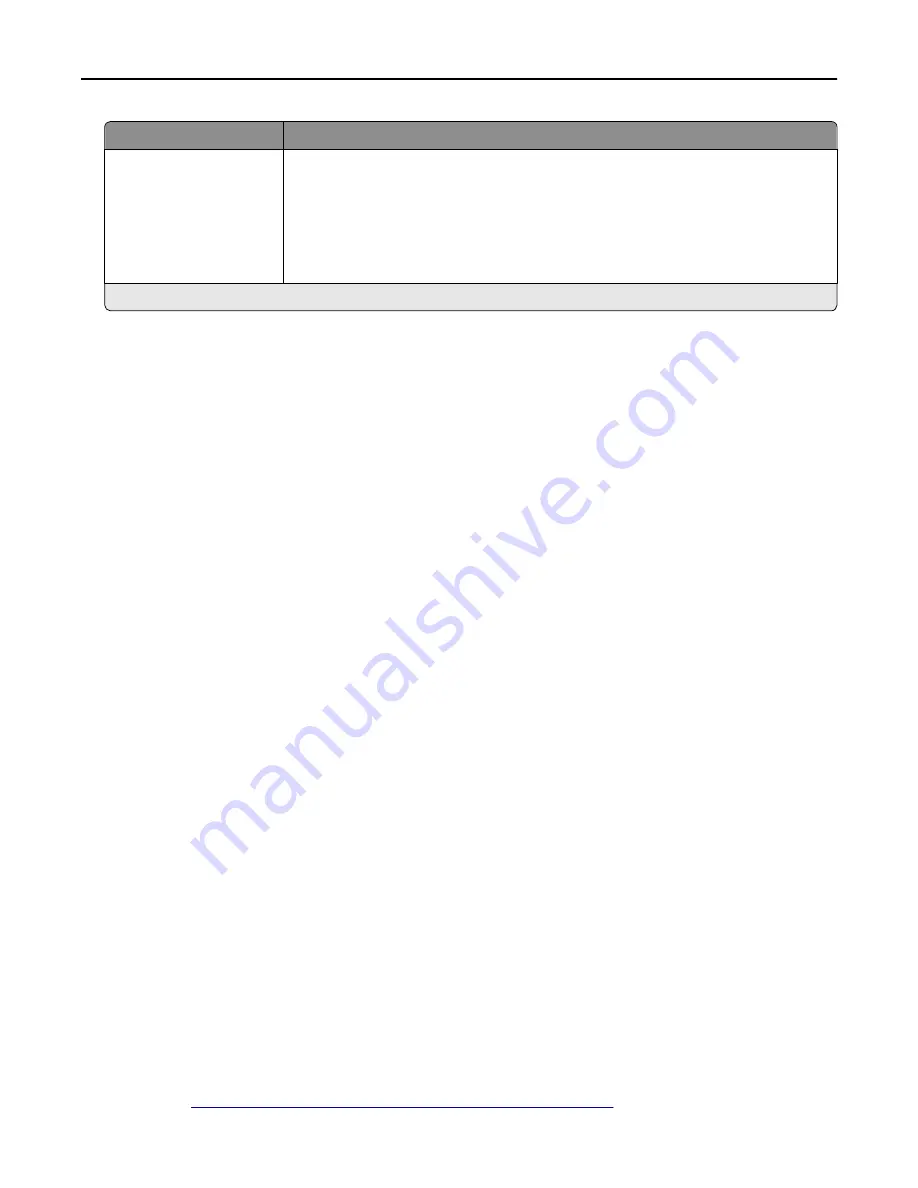
Reserve Job Expiration
Off
1 hour
4 hours
24 hours
1 week
Set a limit on how long the printer stores print jobs for printing at a later time.
Note:
This setting is available only in some printer models.
Note:
Off is the factory default setting.
3
Click
Submit
.
Setting login restrictions
Note:
This setting is available only in advanced
‑
security devices.
To prevent malicious access to a device, restrict the number of invalid login attempts and require a lockout time before
letting users retry logging in.
Many organizations establish login restrictions for information assets such as workstations and servers. Make sure that
device login restrictions also comply with organizational security policies.
1
From the Embedded Web Server, click
Settings
>
Security
>
Miscellaneous Security Settings
>
Login Restrictions
.
2
Enter the appropriate login restrictions:
•
Login failures
—Specify the number of times a user can attempt login before being locked out.
•
Failure time frame
—Specify how long before lockout takes place.
•
Lockout time
—Specify how long the lockout lasts.
•
Panel Login Timeout
—Specify how long a user may be logged in before being automatically logged out.
•
Remote Login Timeout
—Specify how long a user may be logged in remotely before being automatically logged
out.
3
Click
Submit
.
Enabling and disabling USB host ports
Note:
This setting is available only in some printer models.
USB host ports on devices do the following:
•
Detect and display the files that are stored in the inserted USB mass storage devices, such as a flash drive.
•
Print a supported file from the flash drive or initiate a firmware update.
•
Scan data directly into the flash drive.
•
Access can be restricted or permitted depending on the schedule.
In secure environments, devices can be configured to limit these operations, or to not allow them at all.
Device administrators can disable the front USB port during setup using access control restrictions. Devices have a rear
USB host port designed for card readers and HID devices, such as a keyboard.
To restrict access to the front USB port, apply a security template to the appropriate access control. For more
information, see
“Using a security template to control function access” on page 20
.
Managing other access functions
34






























